First, a few links:
Over on Security Stack Exchange we have discussed this exact case.
Noted security commentator Bruce Schneier has some interesting discussion - and in fact it is a recurring theme.
Most fingerprint readers have independently measured EER of 5%; the
best ones allegedly get down to about 0.2%. That means that when the
system is set to a sensitivity such that it only randomly locks you
out one time in 200 (say, 3 times a year), a crook has a 1 in 200
chance of stealing your car just be swiping his finger on the reader
and seeing if it works by luck.
The Chaos Computer Club in Germany has an excellent piece on how they did this to Dr Wolfgam Schauble, the Home Secretary. (You might want to google translate that link if you can't speak German) - basically they got his fingerprint from a glass, made it more visible using cyanoacrylate (like you will have seen on NCIS or CIS), took a photograph using a digital camera and printed it onto wood glue which could then be attached to their own fingertips.
The problem is that in order for a biometric system to work it needs to reject the wrong finger (or retina or whatever) but allow the right one in a world where nothing is perfect.
Fingers might be presented at a different angle, or pressed a little too hard etc., so a little leeway is required in order to make sure valid users are allowed in. In addition, only a number of points are selected, not the entire fingerprint, which further reduces the accuracy required.
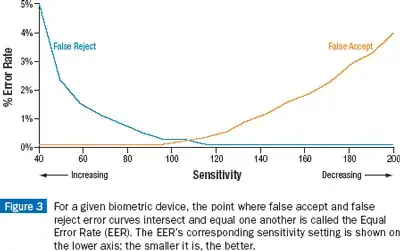
image from http://www.rtcmagazine.com/articles/view/100725
So the trade-off is between false accepts and false rejects - which leads to the possibility of using faked fingerprints, such as a printout, or the amusing gummy bear fingerprints used by Matsumoto.
Matsumoto took a photo-sensitive printed-circuit board (which can be
found in many electronic hobby shops) and used the fingerprint
transparency to etch the fingerprint into the copper. From this he
made a gelatine finger using the print on the PCB, using the same
process as before. Again this fooled fingerprint detectors about 80
per cent of the time.
It is not a jaw-dropping error, it is actually well within design parameters. Biometrics can never be 100% accurate, and in fact if it was it would be useless as a security tool - as soon as your biometrics changed you would be locked out. Have a read of this question on Security Stack Exchange for more information on why biometrics are used as well as username and password, not instead of.
