It's not clear at the moment, because there is no public evidence that a DDoS of any description occurred in Australia on census night. And the people in a position to possess any nonpublic evidence that might exist (ABS/IBM/other authorized operators of the census equipment) have not deemed it necessary to produce it for public scrutiny.
The best we can do is look at the explanation that's being officially put forward, and weigh it against the available circumstantial evidence for plausibility.
Arguments/evidence in favor of a malicious DoS/DDoS
The government says that's what happened. From ABS officials, to MP's and ministers, to the prime minister himself, they've all been relatively consistent in blaming the outage on a malicious DoS. There's been plenty of quibbling and waffling about whether the event was an "attack" or just an "obstruction"/"frustration", and whether or not it should be called "successful". But they all tend to agree that the outage was caused by a malicious (and most typically, "foreign") actor.
Most mainstream news sources (including: Sydney Morning Herald, Australian Financial Review, Sky News, Yahoo News, and others) are not challenging the government's version of events. One expects them to do due-diligence and not report something that the government says is fact unless they've independently confirmed it. That's the point of journalism, after all, and the mainstream journalists say it was what the government says.
Evidence against a malicious DoS/DDoS
Public activity logs show no evidence of a DDoS attack occurring at the time: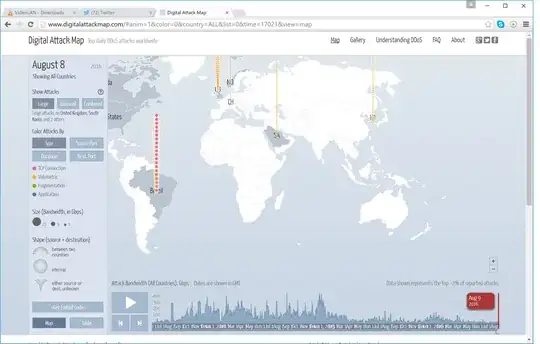 There's some further discussion and analysis of this here.
There's some further discussion and analysis of this here.
Smaller and/or more tech-savvy news outlets (LifeHacker, The Conversation, News.com.au) have published articles questioning the claims about a malicious DoS, and generally concluding that it's at least equally likely that no attack occurred and that the system simply fell over under the weight of legitimate users trying to complete the census.
Load testing done prior to the census going live appears to have underestimated actual demand. According to ABS statements, they planned for 0.5 million submissions per hour, and load-tested to somewhere between 1 million and 1.5 million submissions per hour. There are somewhere north of 12 million households in Australia, about half of which are located on the Eastern third of the continent. And with the census held on a weeknight, most people would be waiting until sometime after 5:00pm AEST to submit it. On that basis, it's easy to see how actual, legitimate demand could have exceeded what was expected and planned for.
A recent ZDNet article, while characterizing the event as a "denial of service incident", attributes the following statement to the PM (albeit without citing where/when the statement was made):
Prime Minister Malcolm Turnbull said today the Census site was not
taken down by a DDoS attack.
"There was some anomalous traffic on the night, that appeared to be
anomalous, actually it was quite innocent it turned out, but that
caused the ABS to take the site down," he said.
"The site was not crashed by denial of service."
Oddly, and quite contradictory, the very same article credits Australian Privacy Commissioner Timothy Pilgrim with stating:
"I am satisfied that personal information was not inappropriately
accessed, lost or mishandled," Pilgrim said in a statement. "The ABS's
decision to shut down the website -- to avoid any prospect that the
DoS attack could include or otherwise facilitate a data breach -- was,
in the circumstances, a pro-privacy precaution."
As time goes on, there seems to be a gradual backing away from claims of a significant attack. On the afternoon of the 11th the Sydney Morning Herald declared the attack(s) "small scale", "not particularly formidable", and "low level" (and if you watch the video accompanying the article, you'll also hear "That raises a couple of possibilities, one is that there were no DoS attacks. The government's maintaining that there are, we have to take them at their word on that.").
And on the morning of the 12th, Sky News is describing the event as a "disruption" that came "from within Australia" and discarding previous suggestions that an overseas DDoS attack occurred.
Also on the 12th, News.com.au published an article criticizing the system for underestimating the anticipated level of demand, and also pointing out that in previous online censuses (censii?) legitimate traffic was misinterpreted as a DDoS attack by a number of ISPs.
A subsequent Sydney Morning Herald article notes IT analyst Kevin Noonan casting doubt on the idea of a malicious DoS occurring or succeeding:
The attack was either a foreign or locally planned denial of service,
or just a "large load" that appeared to be a denial of service but was
in fact people trying to fill out the Census, he said. It "beggars
belief" IBM's data centre could not handle a denial of service attack,
he added.
As the official story continues to evolve, it's worth keeping the timeline of events in mind. The ABS says they took the census offline at 7:30 PM on the 9th. However twitter indicates sporadic reports of outages from as early as 9:41 AM on the 9th, with a significant uptick from about 6:00 PM on the 9th (see also: 1, 2, 3). I personally tried to access the census several times between 6:30 and 7:00 PM AEST on the 9th, and could not (I'm on NBN fibre, so the problem wouldn't have been at my end).
Nobody has claimed that the DoS attack continued past 7:30 PM, however it took nearly a full 48 hours before the census was brought back online. A malicious DoS attack is something that should be quickly addressable (particularly given the more recent reports downplaying the size and impact of the DoS).
An ITWire article on Sunday notes that reports of problems accessing the census have continued since it was restarted, despite geoblocking now being enabled (the site reports as down because downforeveryoneorjustme.com is hosted in the U.S.) and a relatively lower volume of forms being submitted since it came back online (2.33 million forms were submitted on census night before the server went offline at 7:30 PM, versus 405,000 in the first 18 hours after it came back online) and no claims involving new DDoS attacks:
Complaints continue even today, with Guardian Australia political
columnist Katharine Murphy saying on the ABC's Insiders programme on
Sunday morning that she had tried to submit her form on Saturday, but
was unable to do so.
The same article notes former Australian Bureau of Statistics chief Bill McLennan pointing out that even the ABS system designed to handle requests for paper forms was basically crippled by the amount of legitimate requests it was receiving (emphasis mine):
McLennan said he had had personal experience with this system. "I rang
at different times over one day and couldn't get into the system. In
the end I arose from my slumbers early one morning and rang the number
at 03:45, and the system worked like a charm - as it should because no
people were involved! I would now put my money this problem being
caused by bad estimation of the demand, and that is just bad
management."
Note that the system being discussed in that case is separate from the online census system, however still a good example of an ABS system that was rendered unusable by the sheer volume of legitimate requests and not as the result of any sinister/malicious action.
On the 15th, Media Watch did an excellent piece on this issue, pointing out both the dodgy coverage by many mainstream news outlets, the blatantly conflicting stories put forth by the government, and the lack of any evidence supporting any of them. I recommend just watching it in its entirety; it thoroughly rubbishes claims that China and Russia were responsible for any DDoS activity, and includes this little gem:
Well it may turn out the Chinese were behind it, but was there any
evidence for the claim? And can we be sure the census computers were
actually subject to a major attack?
The answer? No, and no.
I think we're done here.
Conclusion
My conclusion is that there was no malicious DoS attack on the census. #6 is the real clincher for me. We know there were problems accessing the census prior to when the ABS says they took the system offline. There's approximately an hour and a half of downtime unaccounted for, with the most likely explanations being a malicious DoS attack or too much legitimate load on the system. If we take Turnbull's #4 statement that "the site was not crashed by denial of service" at face value, the only remaining option is that it was crashed by legitimate traffic.
So there was, in technical terms, a denial-of-service that occurred. But that was more likely the result of millions of Australians all trying to complete the census at around the same time(s) and the census IT systems being underprovisioned (or poorly implemented and managed).
There's no actual evidence at this point of any malicious actions being taken by domestic or foreign actors against the Australian census. Such claims appear to be based purely upon government say-so, with zero independent verification taking place and observable facts which contradict the government's story. And those claims have been gradually tempering in a way that downplays the role and size of any alleged malicious DDoS attack.
Parting Thoughts
If we were to further examine the less tangible aspects of the issue, we would also find that this incident presents the government and the ABS with significant motivation for dishonesty while not really providing a malicious actor with much motivation for attacking the census (not with a DDoS at least). We'd also see that the timing of the 4 alleged DDoS attacks tended to strongly coincide with times when large numbers of Australians would be attempting to complete the census, and the possible use of an obfuscating scapegoat in claims that geoblocking failed as a DDoS mitigation strategy (which it just plain isn't).
There's also some keen irony in the demands for honesty levelled upon the Australian population by the ABS, and the blatant and brazen manner in which they appear to have lied to the entire population of Australia about what happened.