I have heard claims that anti-malware software isn't really effective and will "only catch 33% of malware", and so it's best to "get rid of them; you don't have to pay, and your system will be faster".
It is right here on my favorite blog, Coding Horror:
Not only does anti-virus cripple your machine's performance, it doesn't even protect you adequately!
A quote Jeff uses in his article from here:
Let me give you the answer: it is 33%. In other words, the average detection rate of malware from these "solutions" was 33%, with the maximum at 50% and the minimum at 2%. Keep this number in mind, that shiny anti-virus product you just bought might be protecting you from just 2% of currently active and common malware (not some esoteric and custom uber-haxor stuff)!
EDIT: I found this, and it looks like 60% is the highest "new malware" detection rate. I do not know if they are scanning or actually protecting you real-time, though.
While it is true that the second best protection is your brain (the best being not turning your computer on at all), my PCTools SpywareDoctor with Antivirus has caught some trojans; it even cleaned it of a Rogue Antivirus application. Mind you, it definitely slows my system down noticeably, but I'm happy enough for now ("640K ought to be enough for anybody.") so I have switched to the best Antimalware program in history, avast!, which is the fastest program with a >95% detection rate.
The brain argument doesn't always hold true for non-geeks (even if they may have some amount of brains). One I considered to be tech-savvy (somewhat, at least) stared at a web page saying "Your computer is infected!" for a minute at school, in IT class, throwing his hands up in exasperation, and getting every other student to look at it. (I of course, having been infected by Scareware before, immediately recognized it, and told him to close it.) He continued to be exasperated until the teacher came around and told him to close it. He did (too late, of course), and a few minutes later, it took over the Windows XP computer.
For geeks (and other people with brains), how true are these claims [con-AV]? What about "normal" people?
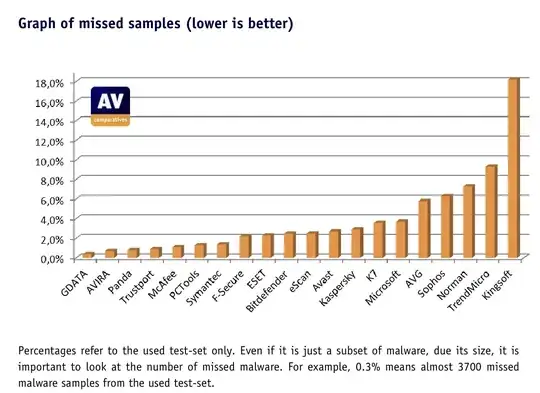
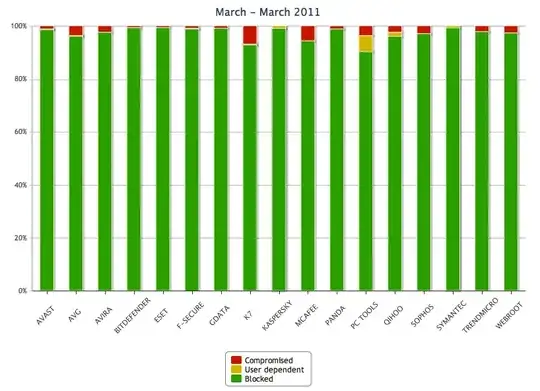 It also shows quite a high detection rate.
It also shows quite a high detection rate. Once a program is executed there is no way of having any guarantee that is not a virus, This is a mathematical fact that is thought in Introductory Computer Science courses. c.f. :
Once a program is executed there is no way of having any guarantee that is not a virus, This is a mathematical fact that is thought in Introductory Computer Science courses. c.f. :