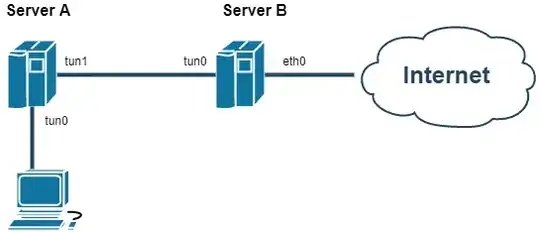
Here's the rough picture of what I'm trying to do:
client -> |VPN| -> server A -> |VPN| -> server B -> Internet.
Server A and Server B are both on public internet with public IPs, also I have root access to both servers. Client is behind firewall but can reach server A. Client CANNOT reach server B directly. Server A can reach server B. Server B is where I want packets to exit to internet from. I need to encrypt both communications from client to A, and from A to B, since A and B aren't in a common LAN so traffic between A and B travel via public infrastructure.
I have been able to setup a IPSec VPN server on A and are able to connect to it. But I can't figure out the correct way to establish another VPN from A to B and reroute traffic coming to A from client to B.
Tips?
p.s. originally I thought of using SSH tunnels to connect A and B then route relevant packet from client arriving at A to B via such tunnel. But as people pointed out in comments that this isn't such a good idea. So I'm open to any suggestions. Thanks!
EDIT #1
VPN service on server A is setup with strongswan, which handles any connection between clients and server A. I was done via ipsec.conf:
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2"
strictcrlpolicy=no
uniqueids=yes
cachecrls=no
conn ipsec-ikev2-vpn
auto=add
compress=no
type=tunnel # defines the type of connection, tunnel.
keyexchange=ikev2
fragmentation=yes
forceencaps=yes
dpdaction=clear
dpddelay=300s
rekey=no
left=%any
leftid=47.112.200.xxx # if using IP, define it without the @ sign
leftcert=vpn-server.cert.pem # reads the VPN server cert in /etc/ipsec.d/certs
leftsendcert=always
leftsubnet=0.0.0.0/0
right=%any
rightid=%any
rightauth=eap-mschapv2
rightsourceip=10.10.10.0/24 # IP address Pool to be assigned to the clients
rightdns=1.1.1.1,8.8.8.8 # DNS to be assigned to clients
rightsendcert=never
eap_identity=%identity # defines the identity the client uses to reply to an EAP Identity request.
With ufw (the tutorial I followed used ufw but I can work with basic iptables rules as well) settings in /etc/ufw/before.rules; I omitted portion auto-generated by ufw, also I've manually allowed udp on port 500/4500 and tcp on port 22:
#
# rules.before
#
# Rules that should be run before the ufw command line added rules. Custom
# rules should be added to one of these chains:
# ufw-before-input
# ufw-before-output
# ufw-before-forward
#
# Don't delete these required lines, otherwise there will be errors
*nat
-A POSTROUTING -s 10.10.10.0/24 -o eth0 -m policy --pol ipsec --dir out -j ACCEPT
-A POSTROUTING -s 10.10.10.0/24 -o eth0 -j MASQUERADE
COMMIT
*mangle
-A FORWARD --match policy --pol ipsec --dir in -s 10.10.10.0/24 -o eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m tcpmss --mss 1361:1536 -j TCPMSS --set-mss 1360
COMMIT
*filter
:ufw-before-input - [0:0]
:ufw-before-output - [0:0]
:ufw-before-forward - [0:0]
:ufw-not-local - [0:0]
# End required lines
-A ufw-before-forward --match policy --pol ipsec --dir in --proto esp -s 10.10.10.0/24 -j ACCEPT
-A ufw-before-forward --match policy --pol ipsec --dir out --proto esp -d 10.10.10.0/24 -j ACCEPT
This is how far I've got. Separate attempt to setup site-to-site VPN via strongswan IPSec between A and B has failed due to port 500 and 4500 being blocked/tempered with: client can reach A via 500/4500, A cannot reach B via 500/4500, and I've exposed all ports of B to open internet for testing.
EDIT 2
Currently the only tunnel I've managed to make between A and B is a SSH socks (ssh -N -f -4 -D 1080 [server B ip] from server A). I'm thinking about just redirecting traffic exiting A, whose destination isn't my client device, to B via that SSH tunnel.
Something like:-A OUTPUT -p tcp --dport 443 -j REDIRECT --to-ports 1080 in ufw/iptables.(this doesn't actually work, server A's ip still shows up in ip checker and blocked websites are still not accessible)