Disclaimer:
This is not a "I need VPN to surf Netflix". Surfing without VPN at this site allows Netflix.
The question is instead the other way around: "There is a PC that needs to Internet through VPN only, but Netflix detects it is behind VPN. How?"
First things to take into account:
- Netflix allows IPs from this VPN provider.
- We are in Italy.
- We use Italian servers from this paid VPN provider.
- We surf Netflix Italia.
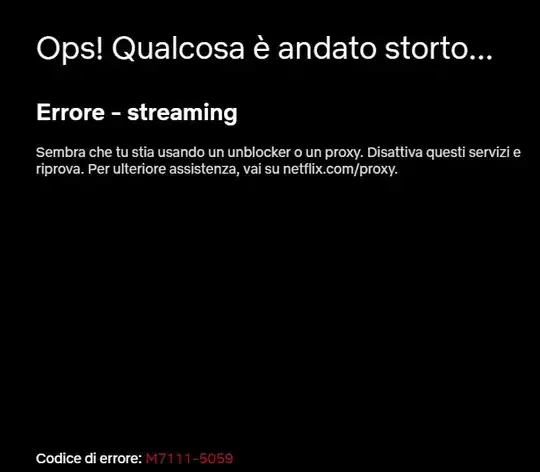
If they connect to Netflix through Machine C, they get the message (translated from italian): "Something went wrong. Streaming error. Looks like you are using an unblocker or proxy, disable those services and retry. Error code: M7111-5059."
Please note that this is not VPN server related. If C connects to the same VPN server used by A, but locally through the provider's VPN app, Netflix will not detect it as "behind an unblocker".
I would like to know what does Netflix detects in this setup that is instead undetected if the VPN app is ran right on machine C?
Can this type of detection be used by someone else (quite sure) with evil intentions? What am I actually revealing with my setup that stays undetected when the VPN app is run? How to troubleshoot this?
My customer isn't violating any Netflix's term of service, they just need to surf the web through VPN only, and they would like to use Netflix at lunch break.
I'm not concerned about their inability to watch TV shows at lunch: I'm mainly concerned that my setup could have an hole and others can actually track the real network's details when users do surf through Machine A's VPN.
Following suggestions in the first Answer from Mr. Yevhen Stasiv, I've run WITCH VPN Detector test and it doesn't show relevant differences between Machine A and Machine C's VPN. It only shows two hops less, 7 vs 9. (probably, Machine A and B indeed!!).
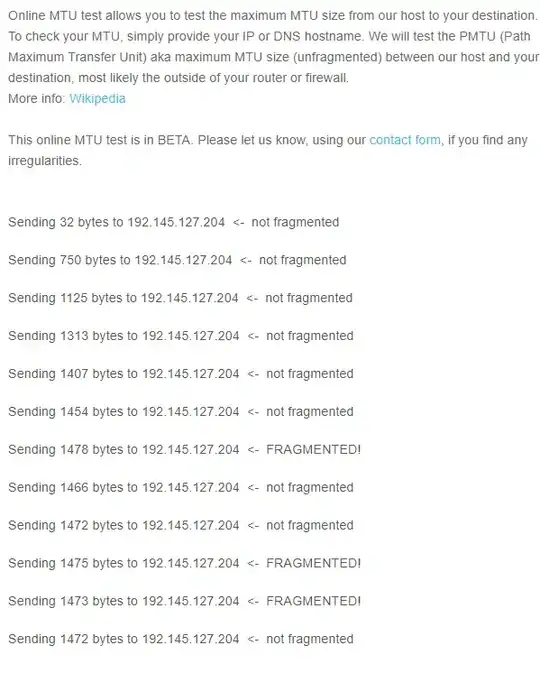
I also tried other MTU related tests, like the one on letmecheck.it and they all return 1472 as biggest unfragmented packet for both Machine A and C VPNs.
Configuration details follows:
At this site there are some PCs (like Machine C in the diagram) connecting through VPN only.
Machine A is an Ubuntu 16.04 box set up as gateway with firewall and VPN client.
Machine B is an IPFire firewall that doesn't do masquerading and has outbound filtering rules only.
A is default gateway for B. B is default gateway for the LAN with problematic PC (Machine C).
The VPN client of A is openvpn and it is connected to a popular paid VPN service.
Host: public/private ip
Provider's router: xxx/192.168.100.1
Machine A: 192.168.100.2/192.168.66.2
Machine B: 192.168.66.1/192.168.77.1
Machine C: 192.168.77.133
Machine A's setup:
Iproute2 config
root@scrrtr:~# cat /etc/iproute2/rt_tables
#
# reserved values
#
255 local
254 main
253 default
100 Tprovider
150 Tvpn
0 unspec
root@scrrtr:~# ip rule show
0: from all lookup local
32757: from 192.168.77.133 lookup Tvpn
32762: from all to 1.0.0.1 lookup Tvpn
32763: from all to 1.1.1.1 lookup Tvpn
32764: from 10.8.1.16 lookup Tvpn
32765: from 192.168.100.2 lookup Tprovider
32766: from all lookup main
32767: from all lookup default
root@scrrtr:~# ip route show
0.0.0.0/2 via 192.168.100.1 dev ens160
0.0.0.0/1 via 10.8.1.1 dev tun0
default via 192.168.100.1 dev ens160
10.8.1.0/24 dev tun0 proto kernel scope link src 10.8.1.16
64.0.0.0/2 via 192.168.1.1 dev ens160
128.0.0.0/2 via 192.168.1.1 dev ens160
128.0.0.0/1 via 10.8.1.1 dev tun0
192.0.0.0/2 via 192.168.1.1 dev ens160
192.168.100.0/24 dev ens160 proto kernel scope link src 192.168.100.2
192.168.77.0/24 via 192.168.66.1 dev ens192
192.168.66.0/30 dev ens192 proto kernel scope link src 192.168.66.2
Iptables config
root@scrrtr:~# cat /etc/firewall/iptables.rules
[...]
-A POSTROUTING -o ens160 -j MASQUERADE
-A POSTROUTING -o tun+ -j MASQUERADE
[...]
-A FORWARD -s 192.168.77.133/32 -i ens192 -o ens160 -j DROP
-A FORWARD -i ens192 -o ens160 -j ACCEPT
-A FORWARD -i ens160 -o ens192 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i ens192 -o tun+ -j ACCEPT
-A FORWARD -i tun+ -o ens192 -m state --state RELATED,ESTABLISHED -j ACCEPT
[...]
I'd like to know how to troubleshoot the difference between Machine A's and Machine C's VPNs. Netflix is just an excuse to find vulnerabilities in this network setup.