Validate PTR records and Bind the Site to a Subnet
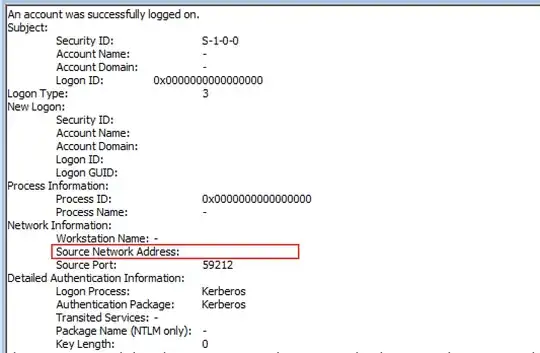
If you would like to see a network address in the log events there are two things you can do to remediate.
1. In the DNS server, validate that you have a reverse lookup zone. If not, create one with the network address of your hosts subnet.
2. Open Active Directory Sites and Services. Drill down through 'Sites > Subnets'. Validate a subnet is created with the network address CIDR for the subnet and that it is bound to the site that exists within that subnet (the one your DC is in).
3. On the DC, open an admin cmd prompt and type 'ipconfig /registerdns'
You should now see the PTR record for your DC is the new DNS Reverse Lookup Zone. If you have additional subnets with hosts in them, create reverse lookup zones for those hosts.
The 'ID 4624 Events (Logon Type 3)' information event should now show the subnet. The type 3 event is when the client accesses the netlogon and/or sysvol shares for logon scripts or group policy enumeration and application.