Summary
I'm trying to figure out what Firewall Policy I need to create to allow VPN connection traffic through my Watchguard firewall.
Description
I'm really struggling to figure out how to create a Site-to-site VPN connection between my Azure VNet and our office subnet.
I've created the VNet, gateways, etc .. as described in this tutorial here. So lets just assume that I've got that right.
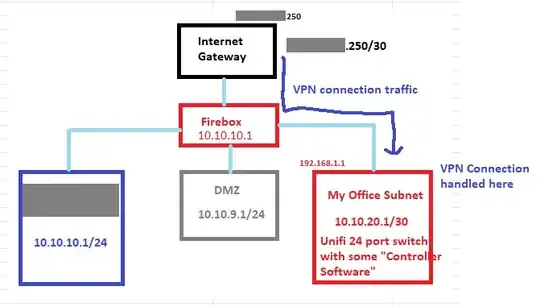
Now, I need to make sure it can access my office subnet which has a Unifi 24 port Switch + Switch-Controller-software which includes some smarts to join/handle the VPN site-to-site connection.
Only problem is, I have a Watchguard Firebox firewall device in between our Fibre internet connection and my office subnet.
I know there's another blog post which explains how to use the Watchguard Firebox as the VPN terminator.
I'm hoping to just forward all VPN traffic through the firebox to my subnet and let my Unifi Controller software handle all of that.
Does anyone have any experience with this sort of thing and can suggest some Policy I need to create to handle this?
Here's a sample picture of our network setup:
So what I thought I had to do was this:
- Create a policy for the Azure VPN Public IP Address (
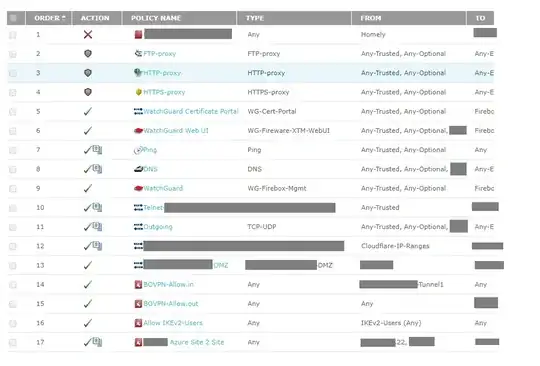
aa.bb.cc.22) in the firewall and push that traffic down to my office subnet (Subnet3). [REFER TO POLICY #17 in this picture]
So - can anyone help?
I can't even see any traffic from Azure VPN trying to hit us. Honestly, I'm not tooo sure what to even check in the watchguard software to see if any traffic is hitting us and then getting handled or rejected by the firewall.
Can anyone please help?