I have the following setup:
Instance A:
security group sgA
sgA inbound rules contains:
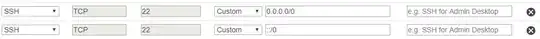
Rule1: * All traffic - All protocols - All port ranges - Source: sgB
Rule2: * SSH - TCP - port 22 - Source: 0.0.0.0/0
Instance B:
security group sgB
Both security groups have 'All traffic' enabled on 0.0.0.0/0 for outbound connections.
With this setup I can ssh from Instance B to Instance A. However, if I remove Rule 2 (the 0.0.0.0/0 rule), ssh now hangs and the machine does not respond to pings.
Am I misinterpreting how ssh access should work based on security groups?