There are two methods (of which I am aware) to achieve this.
First (the easiest), you can add the desired accounts to the scope-specific seuciry group "Remote Management Users" group (the domain group if looking to access domain controllers, or the local group if looking to access a member server or workstation).
Alternatively, you can either register a new PS Session Configuration (Register-PSSessionConfiguration - a process I will not go into), or modify the ACL of the existing default PSSessionConfiguration, Microsoft.Powershell, (Set-PSSessionConfiguration).
To modify the existing configuration, you can either use the SDDL GUI by running the following:
Set-PSSessionConfiguration -Name Microsoft.Powershell -ShowSecurityDescriptorUI
This will pop up a familiar Security dialog to modify the ACL. Depending upon what you are looking to do, you will have to adjust the permissions accordingly. This will have to be manually repeated on each endpoint.
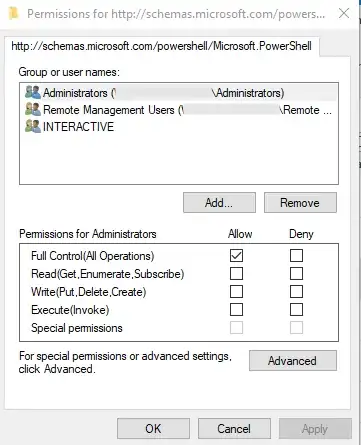
Or, if looking to script the changes to multiple endpoints, you can use an SDDL string. Depending upon your familiarity with the SDDL syntax, this could prove more challenging, but it will allow you to "deploy" the change easily.
Set-PSSessionConfiguration -Name Microsoft.Powershell -SecurityDescriptorSddl "O:NSG:BAD:P(A;;GA;;;BA)(A;;GA;;;RM)(A;;GXGR;;;S-1-5-21-XXXXXXXXX-XXXXXXXXX-XXXXXXXXX-XXXXX)(A;;GA;;;IU)S:P(AU;FA;GA;;;WD)(AU;SA;GXGW;;;WD)"
The above SDDL translates to the default settings (captured in the image above) with an additional entry for an AD object with the Read & Execute permissions.
S-1-5-32-580 is the well known SID for the Remote Management Users Group.
<SCOPE>\Administrators: Full Control
<SCOPE>\S-1-5-32-580: Full Control
<SCOPE>\<Principal>: Execute (Invoke);Read(Get,Enumerate,Subscribe)
INTERACTIVE: Full Control
