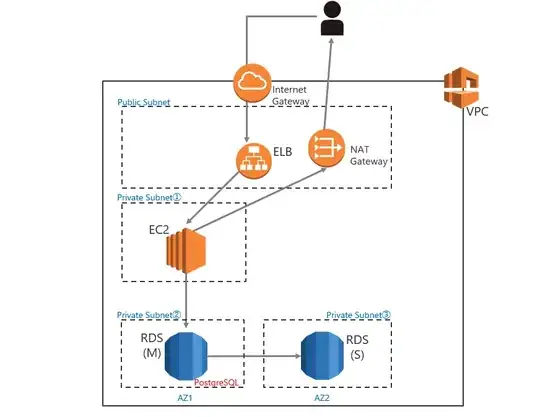
I'm trying to build a system like this one:
I can't connect to the Instance in private public through ALB. I checked my cloudformation code several times and still couldn't find problem. Please help me.
AWSTemplateFormatVersion: 2010-09-09
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: "system"
Parameters:
KeyNameA:
Type: AWS::EC2::KeyPair::KeyName
SSHLocation:
Type: String
MinLength: 9
MaxLength: 18
Default: 0.0.0.0/0
AllowedPattern: (\d{1,3})\.(\d{1,3})\.(\d{1,3})\.(\d{1,3})/(\d{1,2})
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 10.1.0.0/16
EnableDnsSupport: True
EnableDnsHostnames: True
InstanceTenancy: default
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-VPC
InternetGateway:
Type: AWS::EC2::InternetGateway
DependsOn: VPC
AttachGateway:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PublicSubnetA:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.1.10.0/24
AvailabilityZone: !Select [ 0, !GetAZs ]
MapPublicIpOnLaunch: True
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-Public-A
PublicSubnetB:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.1.30.0/24
AvailabilityZone: !Select [ 1, !GetAZs ]
MapPublicIpOnLaunch: True
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-Public-B
PrivateSubnetA:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.1.20.0/24
MapPublicIpOnLaunch: False
AvailabilityZone: !Select [ 0, !GetAZs ]
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-Private-A
PublicRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: Public
PublicRoute:
Type: AWS::EC2::Route
DependsOn: AttachGateway
Properties:
RouteTableId: !Ref PublicRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
PrivateRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: Private
PrivateRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateRouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref NATGateway
NATGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt ElasticIPAddress.AllocationId
SubnetId: !Ref PublicSubnetA
ElasticIPAddress:
Type: AWS::EC2::EIP
Properties:
Domain: VPC
PublicSubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnetA
RouteTableId: !Ref PublicRouteTable
PublicSubnetBRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicSubnetB
RouteTableId: !Ref PublicRouteTable
PrivateSubnetARouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnetA
RouteTableId: !Ref PrivateRouteTable
TargetGroup:
Type: AWS::ElasticLoadBalancingV2::TargetGroup
Properties:
VpcId: !Ref VPC
Name: WebInstanceTargetGroup
Protocol: HTTP
Port: 80
TargetType: instance
Targets:
- Id: !Ref WebInstance
Port: 80
ALBalancerSG:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: SG for ALBSG
GroupName: ALBSG
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
ALB:
Type: AWS::ElasticLoadBalancingV2::LoadBalancer
Properties:
Name: PublicALB
Scheme: internet-facing
IpAddressType: ipv4
Subnets:
- !Ref PublicSubnetA
- !Ref PublicSubnetB
SecurityGroups:
- !Ref ALBalancerSG
Listener:
Type: AWS::ElasticLoadBalancingV2::Listener
Properties:
LoadBalancerArn: !Ref ALB
Port: 80
Protocol: HTTP
DefaultActions:
- TargetGroupArn: !Ref TargetGroup
Type: forward
WebInstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: SG for WebInstance
GroupName: WebSG
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
SourceSecurityGroupId: !Ref ALBalancerSG
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: !Ref SSHLocation
WebInstance:
Type: AWS::EC2::Instance
Properties:
BlockDeviceMappings:
- DeviceName: /dev/sda1
Ebs:
VolumeSize: 8
VolumeType: gp2
DisableApiTermination: false
InstanceType: !Ref InstanceTypeParameter
KeyName: !Ref KeyNameA
ImageId: ami-02b7cfebf005c915d
SecurityGroupIds:
- !Ref WebInstanceSecurityGroup
SubnetId: !Ref PrivateSubnetA
PrivateSubnetB:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.1.90.0/24
AvailabilityZone: !Select [ 0, !GetAZs ]
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-Private-B
PrivateSubnetC:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
CidrBlock: 10.1.110.0/24
AvailabilityZone: !Select [ 1, !GetAZs ]
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-Private-C
PrivateRouteTableRDS:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: Private2
PrivateRouteRDS:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateRouteTableRDS
DestinationCidrBlock: 0.0.0.0/0
InstanceId: !Ref WebInstance
PrivateSubnetBRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnetB
RouteTableId: !Ref PrivateRouteTableRDS
PrivateSubnetCRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateSubnetC
RouteTableId: !Ref PrivateRouteTableRDS
DBSubnetGroup:
Type: AWS::RDS::DBSubnetGroup
Properties:
DBSubnetGroupDescription: DBSubnetGroup for RDS instances
SubnetIds:
- Ref: PrivateSubnetB
- Ref: PrivateSubnetC
RDSSGIngress:
Type: AWS::EC2::SecurityGroupIngress
Properties:
GroupId: !GetAtt VPC.DefaultSecurityGroup
IpProtocol: tcp
FromPort: 5432
ToPort: 5432
CidrIp: 0.0.0.0/0
DBMasterInstance:
Type: AWS::RDS::DBInstance
Properties:
DBInstanceIdentifier: DemoRDS
DBName: MyRDS
AllocatedStorage: 10
DBInstanceClass: db.t2.micro
StorageType: gp2
Engine: postgres
EngineVersion: 11.4
MasterUsername: DBUser
MasterUserPassword: DBPassword
PubliclyAccessible: False
VPCSecurityGroups:
- !GetAtt VPC.DefaultSecurityGroup
DBSubnetGroupName: !Ref DBSubnetGroup
DBReplicaInstance:
Type: AWS::RDS::DBInstance
Properties:
DBInstanceIdentifier: DemoReplica
AllocatedStorage: 10
DBInstanceClass: db.t2.micro
SourceDBInstanceIdentifier: !Ref DBMasterInstance
SourceRegion: ap-northeast-3