TLD: Error, when the public subnet is inbound, is deny all.
The EC2 instances failed to communicate with AWS Elastic Beanstalk,
either because of configuration problems with the VPC or a failed EC2 instance.
Check your VPC configuration and try launching the environment again.
my configuration
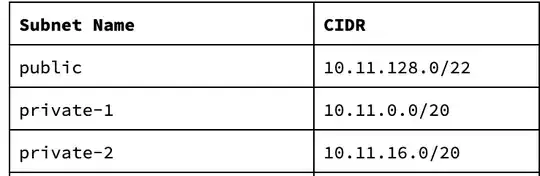
I have three subnets inside a VPC also public is assigned with internet age way and both private subnets are assigned with nat gateway
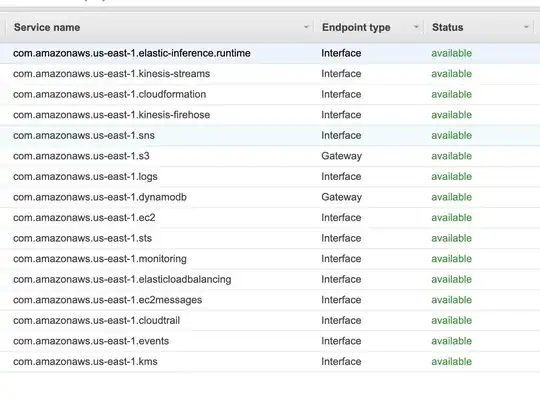
 VPC endpoint services added with SG allowing all traffic from VPC level and added both private-1 and private-2 subnets
VPC endpoint services added with SG allowing all traffic from VPC level and added both private-1 and private-2 subnets
private-1 and private-2 subnets ACL inbound
private-1 and private-2 subnets ACL outbound
Using a cloud formation template deployed a node beanstalk app both ec2 and ELB in the private-1 subnet where ELB is with the internal schema security group allows port 80 on instance from ELB SG.
And after a long wait, the beanstalk app failed with the error
The EC2 instances failed to communicate with AWS Elastic Beanstalk,
either because of configuration problems with the VPC or a failed EC2 instance.
Check your VPC configuration and try launching the environment again.
I allowed ports from public subnet to private-1 and connected through ssh tunnel from instance public subnet into the ec2 instance created by the beanstalk. There are is no configuration done on the instance
- Node app is not running on port 8081
- Nginx is not running on port 8080
- No IP tables forward rule for port 80 to 8080
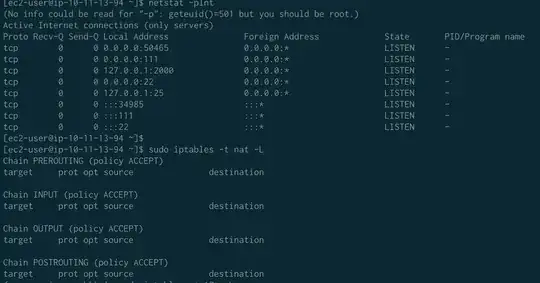
When I allow inbound on public subnet elastic beanstalk app is configured and the environment is green
I don't understand why I need to allow public subnet ACL inbound if I'm not at all using any resource in that and why beanstalk is not configuring the instance in that case?
I still face the issue after allowing 1024-65535 ephemeral ports in public subnet inbound ACL for return traffic from the internet.
Beanstalk able to launch successfully after adding port 443 in public subnet inbound ACL
new ACL for the public subnet
As no network allowed from public subnet to private subnet and the entire setup is in private subnet, why port 443 breaking the beanstalk environment?