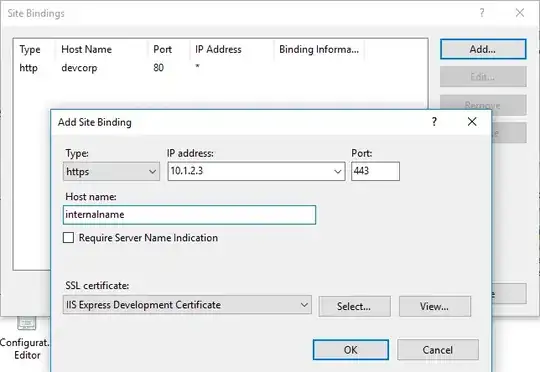
I have a public web server that's also extensively used from the LAN. We're standing up a Windows AD CA server for the LAN side but we'll also need a public SSL Certificate for the web server. The website url resolves to the interal ip on the LAN so I'm assuming I'll need to have both a public certificate and a lan certificate installed at the same time.
How can this be accomplished?