(I first posted this here, but it was suggested to be more on topic here)
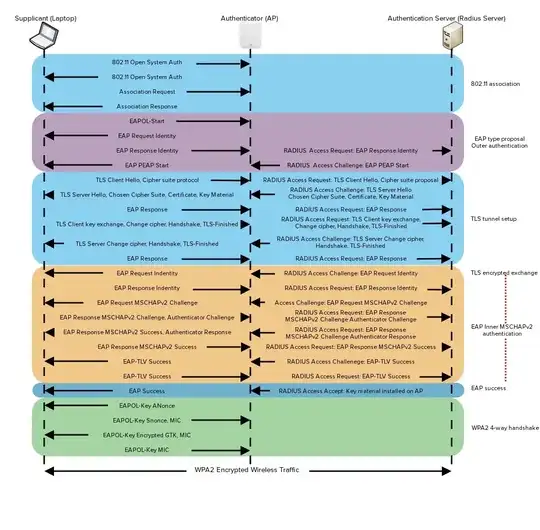
I want to run the "same" WLAN in two independent sites (in different cities) in such a way that a user once connected to the WLAN in City A can easily connect in City B as well. As it turned out, just using the same SSID FOOBAR won't work. For example, in Windows boxes, you have to remove the known FOOBAR and then search again for available WLANs - aparently, the FOOBAR "here" is somehow different from the FOOBAR "there". In a way, it is understandable that just publishing the same SSID name should not be sufficient - after all anybody could just setup popular SSIDs, have walk-by clients attempt to automatically login with their credentials, and collect the data.
While both sites have their own WiFi management (a Sophos UTM), in the background all essentialities should be the same: Authentication is via a common RADIUS server (connected to both sites via tunnel) and therupon by MSCHAP via a common Windows AD server. So my question is: What else that must be kept in sync between my two cities in order to make the WLANs the "same" in a manner sufficient to allow automated connect to the second site the same way one re-connects to the first site? Is it some kind of private key or shared secret perhaps? In another forum, they suggested using the same DNS server IPs in both sites, but this appeared not to work for me. (However, one thing I cannot make the same in both sites is the IP range)
In case the answer depends on the type of clients, I am primarily interested in Windows 10 systems, but also iPhone/Android smartphones.