I'm trying to expose a web server to the internet.
Sockets are apparently ok:
$ ss -tupan -6 state listening | grep node
tcp 0 128 *:7443 *:* users:(("node-default",pid=28327,fd=26))
tcp 0 128 *:7777 *:* users:(("node-default",pid=28327,fd=25))
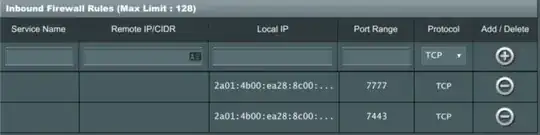
I've exposed ports 7777 and 7443 on my router's firewall and my server's firewalld.
$ firewall-cmd --list-all --zone=home
home (active)
target: default
icmp-block-inversion: no
interfaces: wlan0
sources:
services: ssh mdns samba-client dhcpv6-client samba openvpn
ports: 7777/tcp 7443/tcp
protocols: ipv6-icmp
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
As far as I can tell, HTTP is working fine:
http://[xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx]:7777/]
Unfortunately, so far https is only accessible from inside my LAN:
https://[xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx]:7443
Any idea on what the problem may be / how to further troubleshoot it?
PS: I'm using a self signed certificate for now.
Update 1: iptables rules
$ ip6tables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
14796 14M ACCEPT all * * ::/0 ::/0 ctstate RELATED,ESTABLISHED
1938 155K ACCEPT all lo * ::/0 ::/0
861 98439 INPUT_direct all * * ::/0 ::/0
861 98439 INPUT_ZONES_SOURCE all * * ::/0 ::/0
861 98439 INPUT_ZONES all * * ::/0 ::/0
0 0 LOG all * * ::/0 ::/0 ctstate INVALID LOG flags 0 level 4 prefix "STATE_INVALID_DROP: "
0 0 DROP all * * ::/0 ::/0 ctstate INVALID
20 2013 LOG all * * ::/0 ::/0 LOG flags 0 level 4 prefix "FINAL_REJECT: "
20 2013 REJECT all * * ::/0 ::/0 reject-with icmp6-adm-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all * * ::/0 ::/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all lo * ::/0 ::/0
0 0 FORWARD_direct all * * ::/0 ::/0
0 0 FORWARD_IN_ZONES_SOURCE all * * ::/0 ::/0
0 0 FORWARD_IN_ZONES all * * ::/0 ::/0
0 0 FORWARD_OUT_ZONES_SOURCE all * * ::/0 ::/0
0 0 FORWARD_OUT_ZONES all * * ::/0 ::/0
0 0 LOG all * * ::/0 ::/0 ctstate INVALID LOG flags 0 level 4 prefix "STATE_INVALID_DROP: "
0 0 DROP all * * ::/0 ::/0 ctstate INVALID
0 0 LOG all * * ::/0 ::/0 LOG flags 0 level 4 prefix "FINAL_REJECT: "
0 0 REJECT all * * ::/0 ::/0 reject-with icmp6-adm-prohibited
Chain OUTPUT (policy ACCEPT 15085 packets, 2863K bytes)
pkts bytes target prot opt in out source destination
15681 3011K OUTPUT_direct all * * ::/0 ::/0
Chain FORWARD_IN_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_home all wlan0 * ::/0 ::/0 [goto]
0 0 FWDI_public all + * ::/0 ::/0 [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_OUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_home all * wlan0 ::/0 ::/0 [goto]
0 0 FWDO_public all * + ::/0 ::/0 [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_direct (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_home (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_home_log all * * ::/0 ::/0
0 0 FWDI_home_deny all * * ::/0 ::/0
0 0 FWDI_home_allow all * * ::/0 ::/0
0 0 ACCEPT icmpv6 * * ::/0 ::/0
Chain FWDI_home_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_home_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_home_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public_log all * * ::/0 ::/0
0 0 FWDI_public_deny all * * ::/0 ::/0
0 0 FWDI_public_allow all * * ::/0 ::/0
0 0 ACCEPT icmpv6 * * ::/0 ::/0
Chain FWDI_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_home (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_home_log all * * ::/0 ::/0
0 0 FWDO_home_deny all * * ::/0 ::/0
0 0 FWDO_home_allow all * * ::/0 ::/0
Chain FWDO_home_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_home_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_home_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public_log all * * ::/0 ::/0
0 0 FWDO_public_deny all * * ::/0 ::/0
0 0 FWDO_public_allow all * * ::/0 ::/0
Chain FWDO_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
753 87315 IN_home all wlan0 * ::/0 ::/0 [goto]
34 3461 IN_public all + * ::/0 ::/0 [goto]
Chain INPUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain IN_home (1 references)
pkts bytes target prot opt in out source destination
827 94978 IN_home_log all * * ::/0 ::/0
827 94978 IN_home_deny all * * ::/0 ::/0
827 94978 IN_home_allow all * * ::/0 ::/0
719 80600 ACCEPT icmpv6 * * ::/0 ::/0
Chain IN_home_allow (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:22 ctstate NEW
77 11842 ACCEPT udp * * ::/0 ff02::fb udp dpt:5353 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpt:137 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpt:138 ctstate NEW
1 136 ACCEPT udp * * ::/0 fe80::/64 udp dpt:546 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpt:137 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpt:138 ctstate NEW
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:139 ctstate NEW
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpt:445 ctstate NEW
0 0 ACCEPT tcp * * ::/0 ::/0 tcp dpts:1714:1764 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpts:1714:1764 ctstate NEW
0 0 ACCEPT udp * * ::/0 ::/0 udp dpt:1194 ctstate NEW
16 1280 ACCEPT tcp * * ::/0 ::/0 tcp dpt:7777 ctstate NEW
14 1120 ACCEPT tcp * * ::/0 ::/0 tcp dpt:7443 ctstate NEW
0 0 ACCEPT icmpv6 * * ::/0 ::/0 ctstate NEW
Chain IN_home_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_home_log (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public (1 references)
pkts bytes target prot opt in out source destination
34 3461 IN_public_log all * * ::/0 ::/0
34 3461 IN_public_deny all * * ::/0 ::/0
34 3461 IN_public_allow all * * ::/0 ::/0
14 1448 ACCEPT icmpv6 * * ::/0 ::/0
Chain IN_public_allow (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp * * ::/0 fe80::/64 udp dpt:546 ctstate NEW
Chain IN_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Update 2 - Router Rules:
Router is an Asus DSL-AC68U