I have a 4TB drive that has been bitlocker encrypted (via password) since day one and want to wipe it before I sell it used. The process looks like it's going to take 100+ hours via nwipe but I was wondering if there was any public info on what sectors the bitlocker encryption info is stored so I could just wipe those. As I understand it the password is merely the encryption key for the actual encryption key and the encryption key is stored somewhere on the drive. Anyone have any references to if this is a correct assumption and/or what sectors hold that info so I can just wipe those and sell the drive? Thanks in advance for any help!
-
2What is nwipe? The only thing you should wipe modern SATA drives with is a program that does secure erase. I took a glance at nwipe, and it doesn't seem to have secure erase capability. See [here](https://cmrr.ucsd.edu/resources/secure-erase.html) for one appropriate tool. You may be able to find others as well. – Michael Hampton Jan 25 '19 at 15:37
-
2It's odd to me that someone would buy a used hard drive. You can buy a brand new 4TB SATA drive for $90.00 USD. – joeqwerty Jan 25 '19 at 17:13
-
Question 1: Nwipe is a fork of dban that implements DOD 5220.22M wiping techniques and I'm using the 7 pass in leu of DoD short. The standard is open and thus some people forked the last free version of Dban and turned it into nwipe. – Nuvious Jan 26 '19 at 16:14
-
Question 2: You provide no guidance to the original question. I don't need a new drive. I want to sell this one used for like $40 bucks but want it wiped first. – Nuvious Jan 26 '19 at 16:15
-
@Nuvious Those "standards" were designed for ancient drives made in the 1980s and 1990s. They are utterly useless for modern drives, where a single write pass is sufficient, where overwriting manually as they do will miss various bits of the drive, and where the hard drive can do this properly on its own via the security erase commands. – Michael Hampton Jan 27 '19 at 16:35
-
@MichaelHampton, you are correct in that NIST has replaced the DOD standard with the NIST 800-88 standard. NIST 800-88 CLEAR is what it sounds like you're referring to, however it is for redistribution internally and that's not what's happening. NIST 800-88 PURGE is targeted for drives leaving the organization and involves degaussing (which ruins the drive) or using a secure-erase tool that depends on the modern drive having internal encryption. That leaves a gap since I don't have a degausser or know if the drive supports internal encryption that leads me to go back to the older standard. – Nuvious Mar 02 '19 at 19:16
-
In general you're repeating broad generalizations that were used as bullet points in justifying the change in regulations, but as always the devil is in the details of what the regulations actually say. – Nuvious Mar 02 '19 at 19:17
-
@Nuvious All modern hard drives and SSDs support ATA secure erase or SCSI sanitize. Drives with cryptographic erase are marketed as "self-encrypting" and are easily identified. – Michael Hampton Mar 02 '19 at 19:33
-
@MichaelHampton, you use the term 'modern' without defining it well and after some cursory googling as to what that may mean (specifically how to reliably determine that a drive supports secure-erase) the more the details get fuzzy. First thing I found was that secure-erase should not be done over USB which was the case in this drive (removal from the enclosure would hurt resale value). Additionally investigations into validation of secure-erase have found some drives claim they support it but don't (https://security.stackexchange.com/questions/41676/ata-security-erase-on-ssd). – Nuvious Mar 03 '19 at 15:43
-
@Nuvious Yes, which is why the standard tells you to read the disk again to verify it was actually wiped. I know some drives don't implement secure erase properly; I did that research myself, well before even that 2011 paper. I'm not sure where you're going with this. – Michael Hampton Mar 03 '19 at 15:45
-
Thus for my purpose when processing drives I'll stick to the old mechanic (and in some cases DOD 5220.22M is dictated to me by the person providing the drive). It takes longer; was looking for a shortcut specific to bitlocker but it doesn't seem like a worthy investment of time to figure out vs just running a standard wipe. – Nuvious Mar 03 '19 at 15:47
1 Answers
There are actually multiple keys.
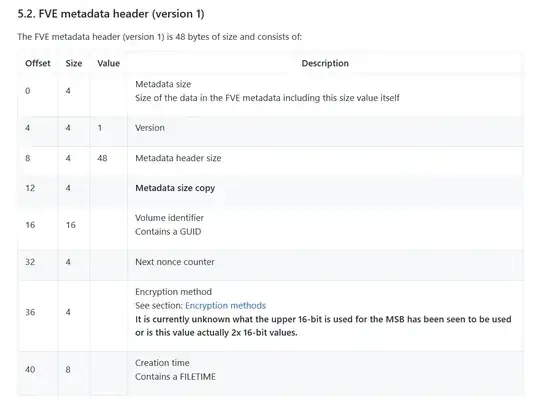
The key used to do the encryption, the Full Volume Encryption Key (FVEK), is stored in the BitLocker metadata on the protected volume. Each sector is encrypted independently.
The FVEK is encrypted using another key, the Volume Master Key (VMK). Three copies of the VMK are also stored in the metadata.
Each copy of the VMK is encrypted using one or more externally-supplied key/password protectors, such as TPM, PIN, User Password, Recovery Password, Recovery Key, Startup Key, or smart card.
The FVEK or VMK cannot be used if the externally-supplied key protectors are not known. So this exercise isn't going to do much for you if protection was not suspended (clear key in use) or the password was weak. It's also likely that the drive is now trashed to the point where it may not be possible to identify the FVEK or VMK in the volume metadata.
You can download a tool to validate the metadata:
More information:
https://www.forensicswiki.org/wiki/BitLocker_Disk_Encryption
libbde - BitLocker Drive Encryption (BDE) format specification:
See section 4, Volume Header. This has the starting location of the FVE metadata blocks. Section 5 has the format of the FVE metadata blocks. Section 5.3 has the FVE metadata types.
- 35,880
- 5
- 54
- 82
-
Thanks for the detailed answer! Went above and beyond what I was hoping to get. – Nuvious Mar 02 '19 at 19:18