I have setup a Client VPN, using steps described in Create a Client VPN Endpoint.
For the server certificate, I picked a public certificate that was newly created and verified by AWS Certificate Manager.
I configured the authentication method to be Use Active Directory authentication with a Directory ID that corresponds to an AWS SimpleAD directory.
I left the Transport Protocol set to UDP.
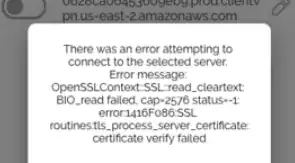
When I download the client configuration and try connecting via Tunnelblick (v3.7.8) on OSX, I get the following error:
VERIFY ERROR: depth=3, error=unable to get issuer certificate: C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Services Root Certificate Authority - G2
OpenSSL: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed
TLS_ERROR: BIO read tls_read_plaintext error
TLS Error: TLS object -> incoming plaintext read error
TLS Error: TLS handshake failed
Any ideas what is not configured correctly or what I could do to resolve this?