You could check client logon for each protocol succeeded or failed via IIS log and event log. Firstly find results of client logon successfully or failed on the event log ,then you could check the detailed information for user accounts and protocols through IIS log.
1.Event log
Event log in Exchange would record client logon status. You could go to Windows Logs -> Security section, the logs record client logon status.
(a).If a user account logon client successfully, an event id 4624 would be generated.
(b).If a user account logon client fails, an event id 4625 would be generated.
 2.IIS log
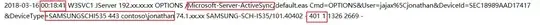
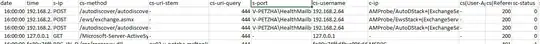
Then, we could see the specific user access time, user name ,logon type and logon status through IIS logs. IIS logs location is below:
C:\inetpub\logs\LogFiles\W3SVC1
To view IIS logs on Exchange more clearly, I recommend you to use Excel to import the logs and then analyze them with different columns. Here are the specific steps:
2.IIS log
Then, we could see the specific user access time, user name ,logon type and logon status through IIS logs. IIS logs location is below:
C:\inetpub\logs\LogFiles\W3SVC1
To view IIS logs on Exchange more clearly, I recommend you to use Excel to import the logs and then analyze them with different columns. Here are the specific steps:
(a).Remove headers starting with a # character in IIS logs.it's convenient to form columns when you open with Excel.
(b).Open an empty Excel spreadsheet and click File> Open, select IIS log. After opening, select the Delimited filter type. Next, select Space and click on Finish. There are some codes listed in IIS log:
• Date (date)
• Time (time, timezone (GMT) )
• Client IP Address (c-ip)
• User Name (cs-username)
• Method (cs-method)
• URI Stem (cs-uri-stem)
• URI Query (cs-uri-query)
• Protocol Status (sc-status)
• Win32 Status (sc-win32-status)
• Bytes Sent (sc-bytes)
• Time Taken (time-taken)
• Host (cs-host)
• User Agent (cs(User-Agent))
• Referer (cs(Referer))
In the code "cs-status", 200 OK success status response code indicates that the request has succeeded(logon successfully). 401 unauthorized client error status response code indicates that the request has not been applied because it lacks valid authentication credentials for the target resource(logon failed).
 More references, please see :https://blogs.msdn.microsoft.com/friis/2014/01/09/how-to-use-excel-to-analyse-iis-logs/
More references, please see :https://blogs.msdn.microsoft.com/friis/2014/01/09/how-to-use-excel-to-analyse-iis-logs/
3-1.For Outlook Web Access, we could check event log mainly, it Accurately records logon time, account name andlogon status. The IIS log also recorded logon status, logon time and logon type.
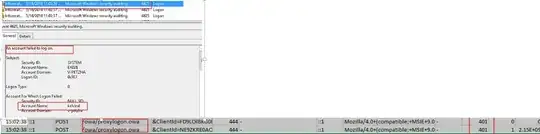
3-2.For Outlook Anywhere, in Exchange Server 2016, MAPI over HTTP is enabled by default at the organization level. But, Outlook clients that are not MAPI over HTTP capable can still use Outlook Anywhere (RPC over HTTP) to access Exchange through a MAPI-enabled Client Access server. We could check event log mainly, it recorded logon status, account name and logon time. The IIS log also accurately records logon time, logon type and login status.
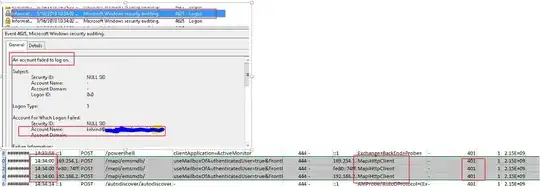
3-3.For Exchange Activesync, We could check event log mainly, it recorded logon status, account name and logon time. The IIS log also accurately records logon time, logon type and login status.