I have a device that needs to have its' bitlocker recovery backup up to AD for visibility in the "Bitlocker Recovery" tab of the object in Active Directory.
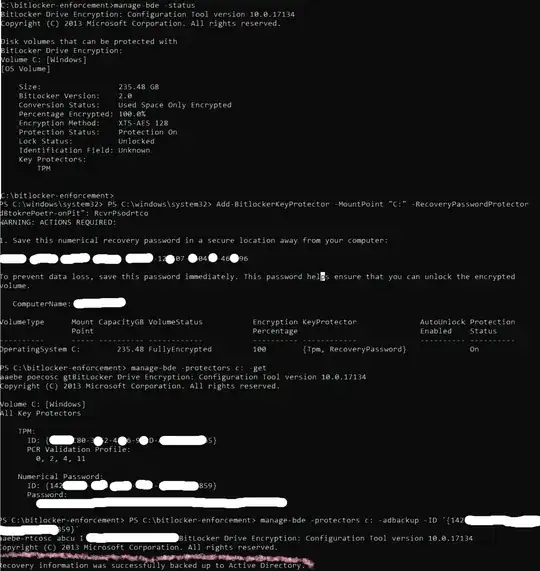
I found that the device only had a TPM protector. So I added a Numerical Password. I want to backup this numerical password to AD.
I run manage-bde protectors c: -adbackup -ID '{my-id-goes-here}'. Windows replies with:
Recovery information was successfully backed up to Active Directory.
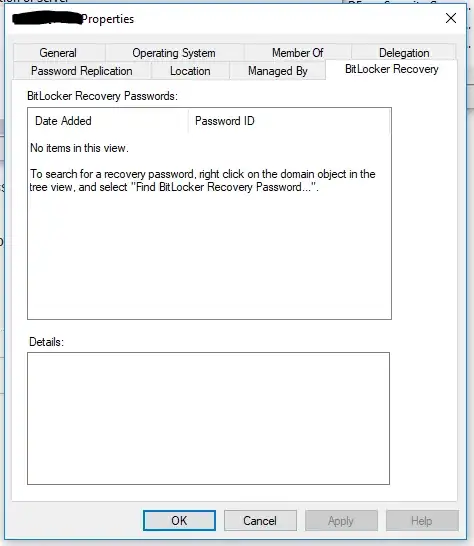
I pull up ADUC, find the device, look at it's 'Bitlocker Recovery' tab only to find that there is nothing here.
I also tried:
$BLV = Get-BitLockerVolume -MountPoint "C:"
Backup-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId
getting a 0 exit code, but nothing published to AD. Is there something I'm missing here?
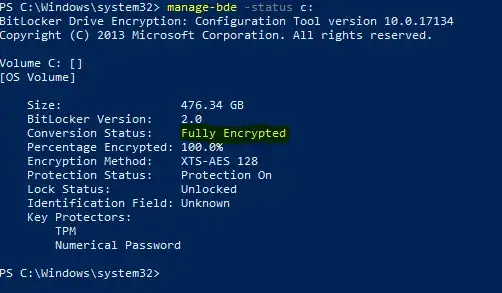
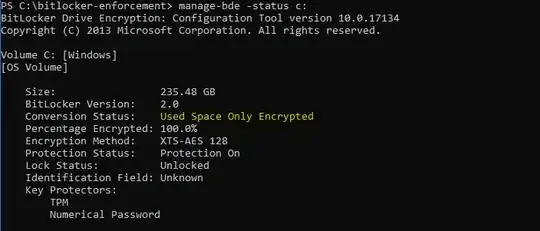
There only difference I see between machines that CAN Have it pushed to AD this way and this device is the 'Conversion Status' field:
A machine that works is 'Fully-Encrypted' instead of 'Only Used Space'.
How can I get this password backed up to AD?