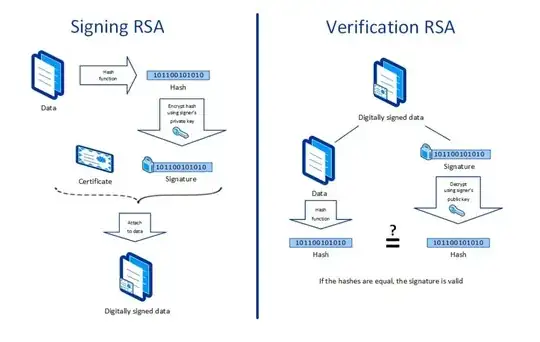
I'm having some trouble creating a certificate with the openssl commandline tool.
The specs for the private key are:
"A digital signature using an RSA 1024 bit key with a SHA-1 hash function (RSA-SHA1-1024)"
Creating it as follows
openssl genrsa -out rsa.key 1024
Generating the CSR
openssl req -new -key rsa.key -out csr.csr
The certificate has the following spec:
- Format = x.509
- Charset = UTF-8
- Encoding = Base-64
- Endianness = Little Endian
- OAEP Padding = PKCS1 v1.5 padding
- Private key size = 1024 bits
- Hash Message Format = SHA-1
I've tried tons of combinations of the following:
openssl x509 -req -utf8 -enc base64 -pkcs -sha1 rsa:1024 -in csr.csr -signkey rsa.key -out server.crt
I can't get a large set of combination of the above command to work at all, always some parameter that breaks it.
According to the spec we're supposed to sign a RSA message digest with the given certificate. I'm a bit confused why and how we are supposed to do this, maybe its an erroneus specification?
I'm using OpenSSL 1.1.0f 25 May 2017
The endianess i can't even find how to set it with the openssl commandline tool, any help here would be greatly appreciated!