Tunnels work on different layer and you can't bond them like physical interfaces. For simply failover, your tunnels will work as is: they all have the same routes.
If you need more flexibility for using all the possible throughput of the interfaces, you can:
- Use NIC bonding on the interfaces.
- Use 802.1Q VLAN tagging for the subnets. This way any subnet can use any NIC.
Use a single VLAN for a single VPN tunnel. As you can see from the picture (where the heights depicts the network capacity in use), your tunnel will be able to exceed the capacity of a single physical NIC despite being a single virtual network interface.
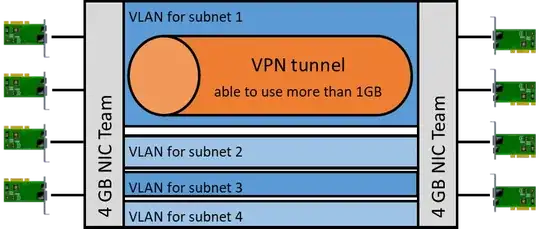
For redundancy, you can configure your tunnel to reconnect on another subnet, if VLAN 1 fails. However, if both servers are connected to a single switch, the only single point of failure would be the switch. If any of the NICs, any switch port or any cable fails, the rest will handle all the L2 subnets including the one having the tunnel.
In other words, while your suggestion tries to add redundancy for this VPN tunnel alone, this solution adds redundancy for all the physical networks, too. The redundancy of your VPN tunnel is now based on this (rather than to the hack suggested in the comments).
