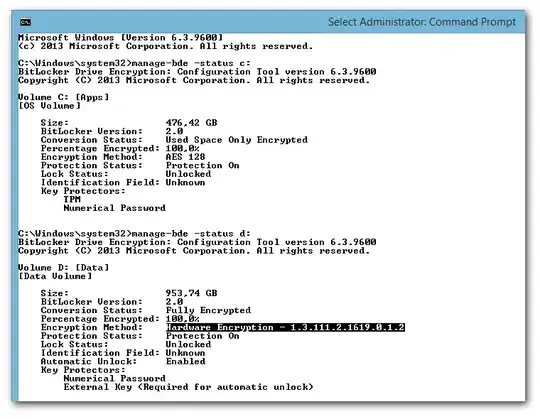
Due to the recent security findings in that probably most SSDs implement encryption in a completely naive and broken way, I want to check which of my BitLocker machines are using hardware encryption and which ones are using software.
I found a way to disable the use of hardware encryption, but I can't figure out how to check if I'm using hardware encryption (in which case, I'll have to re-encrypt the drive). How do I do ti?
I'm aware of manage-bde.exe -status which gives me an output such as:
Disk volumes that can be protected with
BitLocker Drive Encryption:
Volume C: [Windows]
[OS Volume]
Size: 952.62 GB
BitLocker Version: 2.0
Conversion Status: Used Space Only Encrypted
Percentage Encrypted: 100.0%
Encryption Method: XTS-AES 128
Protection Status: Protection On
Lock Status: Unlocked
Identification Field: Unknown
Key Protectors:
TPM
Numerical Password
but I don't know if the information I want is in this screen.