Firstly, the Virtual Network Service Endpoints for Key Vault feature is still in preview. It is strongly recommended to not use this feature for any production scenarios.
In this case, you may need to allow the connection from the virtual network or Public IP address ranges which your application located in to bypass the firewall.
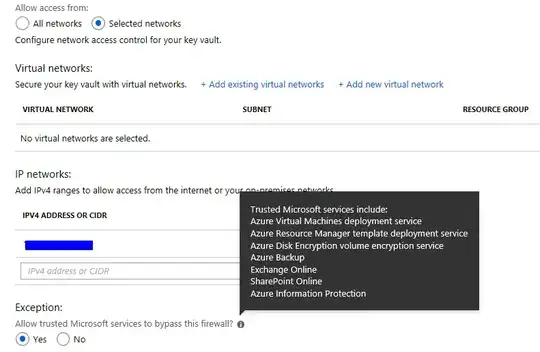
According to your picture access policies, you deny access to traffic from all networks. Any caller outside those sources will be denied access except the default Trusted Microsoft services. Which means these connections from those services will let through the firewall, but such callers still need to present a valid AAD token and must have permissions to perform the requested operation.
Also, App Services is coming soon, I can not find it in the current Trusted Microsoft services. For App Services only ASE (App Service Environment) instances are supported.
Ref: Announcing Virtual Network Service Endpoints for Key Vault (preview)
Update1
From this link you provided in comment.
If you want to restrict network access to PaaS resources, you may make sure you enable the specific service endpoint- Microsoft.KeyVault in your specific subnet. Also, the subnet is allowed if you selected networks. You can get more details from this tutorial.
If you use Azure Managed Service Identity in App Service, you need to make sure you have added an access policy that includes your application's identity. Refer to this.
Update2
In this case, if you just want to allow the web app access to the key vault instead of access the key vault from the on-premise network, you need to add the outbound IP addresses of the web app service to the key vault firewall.
