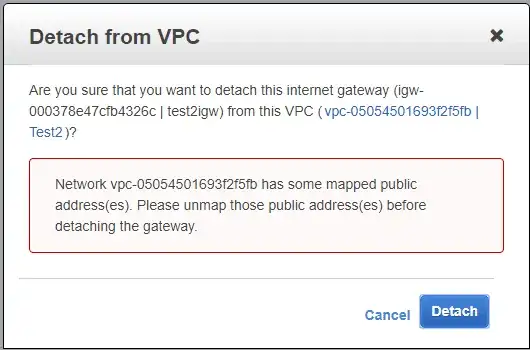
I’m confused about Internet Gateway in AWS, if it says that in order for your VPC to access the internet you need a IGW why then when you create a EC2 instance with an EIP you automatically have access to the internet.
I then have this question that I haven't been able to answer:
Why then when you create an EC2 instance (which is created in the default VPC) in AWS and you assign an elastic IP you automatically have access to the internet if in the AWS documentation says that in order for your VPC to have access to the internet you need an Internet Gateway?