When I connect to a Amazon instance running Windows Server 2003 R2, mstsc says, that it can't verify remote server's identity. Like on this image:
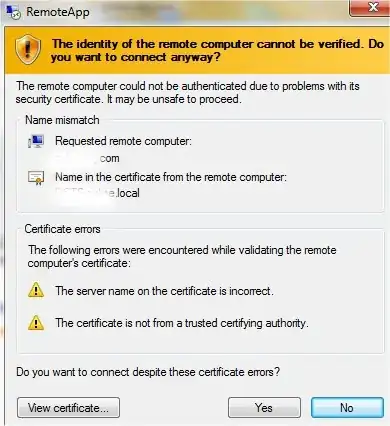
But in my case the certificate name is: i-0e427eaa3f0b7ca11. The issue is not with Amazon infrastructure, isn't it?
My conjecture is that each Amazon instance gets created from some prearranged image. And that's the reason why I've got to reissue the certificate. I've found instructions on how I do that. But they go basically like this: delete some files, reboot, profit. Is that how one generally reissues a certificate? Would this even solve my problem?
UPD I've discovered the certificate (and a lot of other certificates with similar names) in MMC > Certificates (Local Computer) > Personal > Certificates. On the other non-Amazon server I see no certificates in this folder. The certificate has full computer name as a friendly name (but not as a subject). And it's not really clear, what makes the server choose this particular certificate. I suppose I can't delete it. It's probably used for some technical reasons by Amazon.
Generally, the question is, what's going on? How the certificate is chosen? How can I influence it? Who does that? When no certificates in Personal folder, non-TLS connection is established?