I find endless resources on the web explaining well how to restrict access to a computer depending who is trying to log-in. That doesn't allow to control what account will be used to log-in onto the local machine and what is done on that machine. That fact rises some safety concerns.
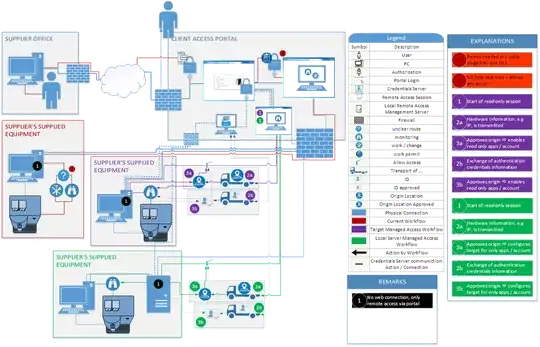
The situation is, that we have software on IPCs (Industrial PC) that allows only monitoring but also a service software what allows to alter the availability of supplied machinery. As we currently cannot ensure that only a certain account or application is used, as we have to log-in via client supplied remote access portal/terminal server, we have to apply for a work permit each time we would like to monitor the system, even for only transferring logger data. Installing another IPC isn’t an option as this particular machine is offshore, so we would like to get it solved software wise.
So that is what we like to realize:
Local read and write user account per IPC
Some accounts allow only to use read only software, such as monitoring software. Others accounts allow to use more function software up to packages what could shut down the machinery.
In our opinion, using different accounts is the most practicable way otherwise a local 3rd party software has to set permission by Windows Policies.Control which accounts can be used
Which local user account (or policy setup in active) depends on from where the remote access request is coming from only- Local access management server
Currently there isn't any central AD controller etc. but if necessary there could be a access master server, e.g. RD Gateway Server or BOMGAR Privileged Access to manage the access permission isolated operation
Our devices are in an isolated network what is behind the clients' network. Properly the most tricky point is to recognize who is requesting access to our isolated network. So far we came up with those ideas:- client network tells our network which account is used but that requires individual clarification of communication.
- our network reads the client IP and decided if it is either read or write access. Client has to be ensure that there are at least two different machine accessing our network. One is for read / permanent access accounts and others for elevated accounts what could require extra access approval by the client
- In case you cannot prevent to log-in as administration into a master server, the administrator account must be managed by the client.
The closest solution I've found so far is this question on super user: Using TeamViewer to login into only one user account but is still far from our requirements.