I currently have a WORKING SFTP login, using a private key for login and the user is chroot'ed into their home directory.
Goal: Keep the user chroot but allow WRITE access to the relative chroot directory, without having to specific any path or cd anywhere.
In other words, when the sftp user logs in, I don't want them to have to cd to another path in order to upload a file.
Due to the chroot directory requiring full root ownership (due to chroot design), I'm not certain if this is even possible.
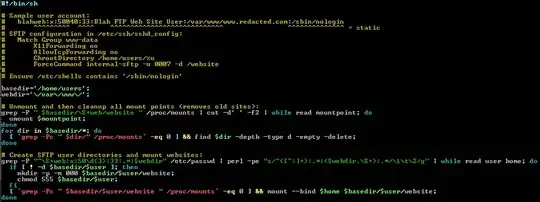
In /etc/passwd:
sftpuser:x:1006:1006:,,,:/home/sftpuser:/bin/false
The users login pubkey is in:
/home/sftpuser/.ssh/authorized_keys
Chroot rules in sshd_confg:
Match User sftpuser
ChrootDirectory /home/sftpuser
ForceCommand internal-sftp
AllowTCPForwarding no
X11Forwarding no
Home dir permissions:
# ls -l /home/ |grep sftpuser
drwxr-xr-x 5 root root 4096 May 4 11:24 sftpuser
# ls -l /home/sftpuser/
total 4
drwxrw-r-x 3 sftpuser sftpuser 4096 May 4 11:23 sftp_share
Example current workflow:
Connected to sftp.example.com.
sftp> ls
sftp_share
sftp> put testfile.txt
Uploading testfile.txt to /testfile.txt
remote open("/testfile.txt"): Permission denied
sftp> cd sftp_share
sftp> put testfile.txt
Uploading testfile.txt to /sftp_share/testfile.txt
testfile.txt
Desired workflow:
Connected to sftp.example.com.
sftp> put testfile.txt
Uploading testfile.txt to /testfile.txt
testfile.txt
Is there any way to allow the upload (put) to the default directory, without having to chdir first?
I do have flexibility to move these directories around. For example, the sftp chroot dir doesn't have to be in the users home directory, I can even change around the users home dir (but the user must still be able to use authorized_keys to login).
Please note: I do understand many SFTP clients, and the command line SFTP client allows for defining a relative path at login. That is out of scope for this question, I'm desiring this config be done server-side and the client simply just needs to login.