I started a TLS1.3-server via openSSL (version 1.1.1-pre4 (beta) 3 Apr 2018 )
$ openssl s_server -key key.pem -cert cert.pem -accept 44330 -www -tls1_3
and a TLS1.3 client
$ openssl s_client -connect 127.0.0.1:44330 -tls1_3
I captured the traffic via wirehark (version: 2.9.0-55):
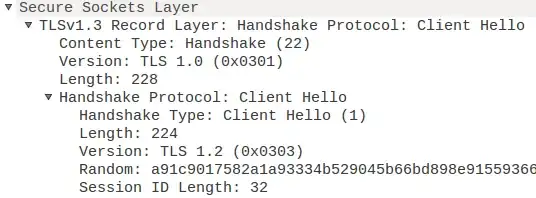
Why is version 1.2 concerning the handshake protocol and even 1.0 for the record layer detected/defined?
While reading the rfc-draft, I found this:
In order to maximize backwards compatibility, records containing an initial ClientHello SHOULD have version 0x0301 and a record containing a second ClientHello or a ServerHello MUST have version 0x0303, reflecting TLS 1.0 and TLS 1.2 respectively.
Looking at my pcap, this record containing a second ClientHello can not be found. And the following ServerHello is indeed version 0x0303.
But it seems, that client and server do speak TLS1.3 after all:
I do not understand this. Can you help me?