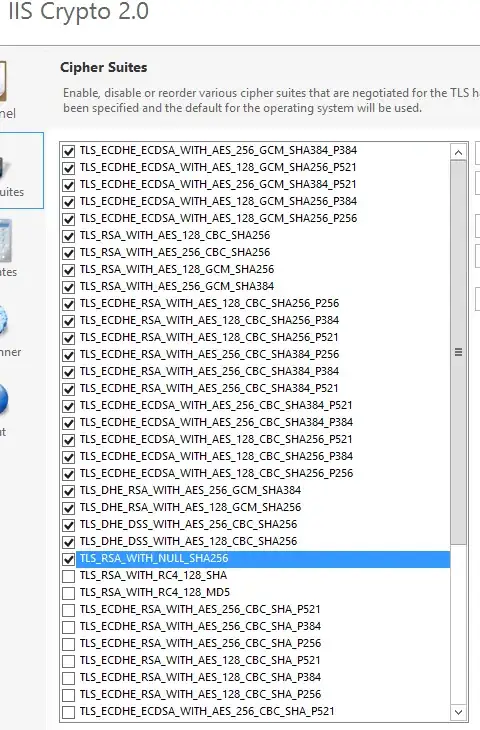
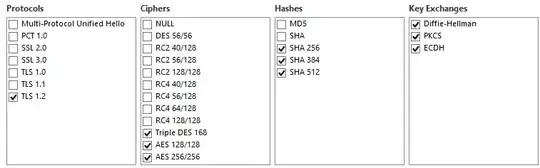
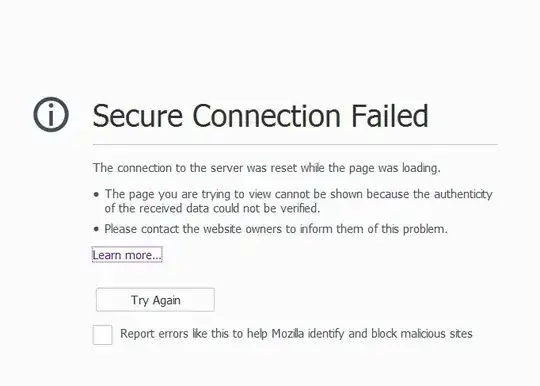
I've been tasked to get our site into PCI compliance by disabling SHA1 on the server. I am accomplishing this by using IIS Crypto 2.0. We decided to also go with just TLS 1.2. the specific problem I am having is when I disable SHA1, all versions of Firefox give the generic error message "Secure Connection Failed". I have enabled all options except for SHA1 and still get the message but as soon as SHA1 is disabled the message comes back. I am pasting screenshots below with the configs on IIS Crypto.
Additionally I have run SChannel ETL and came up with the below results
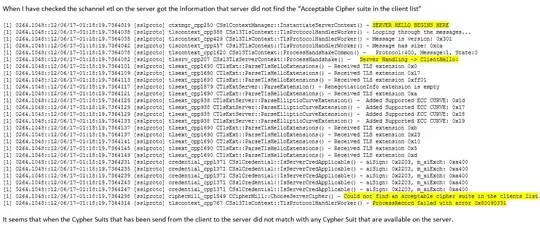
While Running that ETL I ran a Netmon
 as you can see in my config list versus the netmon request I do have those cipher suits enabled yet I am still getting the same error.
as you can see in my config list versus the netmon request I do have those cipher suits enabled yet I am still getting the same error.
I Started on this problem early last month and took a break to work on another project thinking I could come back to this and just figure it out but I am not getting anywhere. I cannot believe that Firefox requires SHA1 to work it just seems ridiculous,
Oh and my Cert Signature is SHA256RSA, My Server is Windows Server 2012 R2 Standard