I am trying to relay SSH connections from LAN hosts to hosts beyond VPN. Only one router host in the LAN has VPN connection to be reused by other hosts in LAN.
Below is pfctl configuration on the router.
extif = "utun0"
intif = "en1"
set skip on lo0
set ruleset-optimization none
set optimization normal
set timeout { tcp.established 360, tcp.closing 60 }
nat log on $extif from $intif:network to any -> ($extif)
pass in log on $extif from any to any
pass out log on $extif from any to any
pass in log on $intif from any to any
pass out log on $intif from any to any
utun0 interface (it has IP address 10.66.20.3) above is interface facing VPN.
LAN host IP address is 192.168.1.34.
Host beyond VPN where I am trying to SSH into has IP address 172.19.13.63.
The problem is router's pfctl performs NAT for SYN packet only, but doesn't return SYN ACK answer of 172.19.13.63 to LAN host.
In the meantime, router successfully NATs ICMP packets from LAN hosts, i.e. 192.168.1.34 pings 172.19.13.63 and I see in tcpdump that NAT is performed by the router.
Below is the result of sudo pfctl -ss during when I am to SSH host (172.19.13.63:22) from LAN host (192.168.1.34): ALL tcp 192.168.1.34:50298 -> 10.66.20.3:37149 -> 172.19.13.63:22 ESTABLISHED:SYN_SENT
tcpdump also confirms that SYN ACK is not forwarded back to LAN host.
What should be changed in pfctl configuration file to make NAT work correctly for SSH connections to hosts beyond VPN?
Below is a screenshot of wireshark snapshot on utun0 interface:
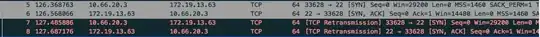
Below is the state in pfctl during SSH connection attempt:
$ sudo pfctl -s all | grep "\.34" | grep tcp
ALL tcp 172.19.13.63:22 <- 192.168.1.34:51856 CLOSED:SYN_SENT
ALL tcp 192.168.1.34:51856 -> 10.66.20.3:42525 -> 172.19.13.63:22 ESTABLISHED:SYN_SENT