I have two servers, one old AD server (server A) and a brand new server (server B). I am trying to migrate from old to new so I setup my second server following these instructions and add the second server as a domain controller within the same domain.
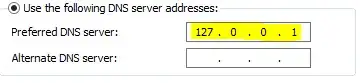
So, everything is wonderful in serverland, both servers are on the old domain and are configured as domain controllers. Now I would like to shut off Server A (eventually will be decommissioned, but I would like to keep it as a backup for now). So I disable AD replication on server B and adjust the DNS settings so that server B no longer points at server A:
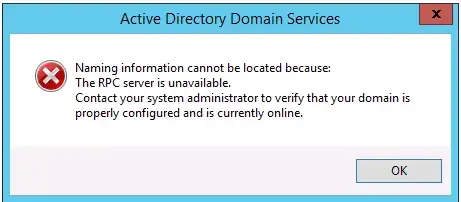
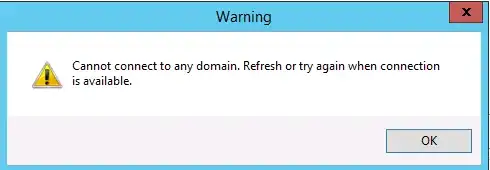
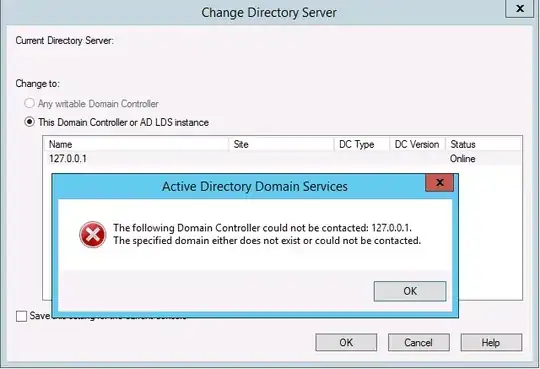
Then I shut off server A. Suddenly(on server B) I cannot access the AD's configuration either through "Active Directory Users and Computers" or "Active Directory Administrative Center". I get various derivations of:
Naming information cannot be located because: The RPC server is unavailable
Cannot connect to any domain. Refresh or try again when connection is available.
The following Domain Controller could not be contacted: 127.0.0.1. The specified domain either does not exist or could not be contacted.
So it seems like its working(I can login with domain credentials, third party applications utilizing AD seem to work), but I can't access anything. Am I missing something here, I don't see why server B doesn't just detect itself as the new AD server. I thought there is no longer a magical "Primary" AD server. Most people on the internet recommend demoting the old AD server, but I'd rather not in this case. Is it possible to complete the AD migration without demoting the old server?
Update 1
After update FSMO roles as @KatherineVillyard suggested I get most of the same errors, but in the "Active Directory Administrative Center" I get one new one that is interesting, when you select "Change domain controller" I get:
Cannot find an available server in the DEV domain that is running the Active Directory Web Service (ADWS).
This is interesting as I checked and I'm sure the service is running on my new box. I wonder if the issue is DNS related. I already tried re-adjusting the network settings and rebooting the server. Often times with these types of issues it seems that I'm just throwing things against the wall and seeing what sticks :(
Update 2
I have tried a great many things, however it seems that I can reproduce the issue by shutting down server A by merely just disabling the NetLogin service on Server A. Once this service on server A stops responding you no longer have access to that domain(similar type errors thrown) through any of the snap-in controls on either server.
I also noticed something funny, when you run the following command on server B:
nltest /DSGetDC:MYDOMAINHERE
You get the following(assuming netlogin is running on both servers):
DC: \\(SERVER A)
Address: \\(SERVER A IP ADDRESS)
Dom Guid: XXXX
Dom Name: (MYDOMAINHERE)
Forest Name: (MYDOMAINHERE)
Dc Site Name: Default-First-Site-Name
Our Site Name: Default-First-Site-Name...
Another thing I notice on the new server(B) is that if you run("dcdiag /test:advertising") you get the following message(no issues on the old server(A)):
Testing server: Default-First-Site-Name\(Server B)
Starting test: Advertising
Warning: DsGetDcName returned information for \\(Server A).(MYDOMAINHERE), when we were trying to reach (Server B).
SERVER IS NOT RESPONDING or IS NOT CONSIDERED SUITABLE.
......................... (Server B) failed test Advertising
This really strikes me as an issue with some sort of DNS configuration on the new server(B), but I've removed every single reference to server A in server B's DNS Manager and rebooted the server. This whole thing is a bit of a black box, where does "DSGetDC" pull this information? The "(DNS) server", which should be server B, which shouldn't have any reference to server A, clearly I'm missing something here :(