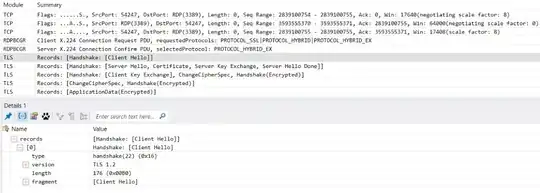
I want to check that my RDP sessions to a windows server 2012 use SSL/TLS 1.0. I found hints about using tools for Windows 2008 that do not exist anymore on Windows Server 2012 and above.
So my question is: how can I be sure (Log--Entries, Session-Monitoring...) that my RDP connection is properly encrypted with TLS 1.x?
Some information: - No server role for remote sessions installed, just RDP for administrative purposes under "System properties" -> "Remote" (NLA required). - In Local Computer Policy Manager I have set the client connection encryption level to "High Level", Require use of specific security layer for RDP connections to "SSL (TLS 1.0)" and Require user authentication for remote connection by using NLA to enabled. - no specific key or certificate created nor installed (I did not manage to find understandable guides on this)
I would like to be sure that encryption actually is used. Thanks a lot! Aurel