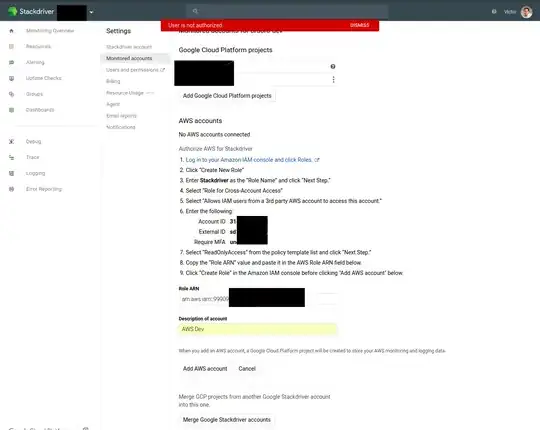
I am following the Stackdriver instructions to add an AWS account to monitor:
Authorize AWS for Stackdriver
Log in to your Amazon IAM console and click Roles.
Click “Create New Role”
Enter Stackdriver as the “Role Name” and click “Next Step.”
Select “Role for Cross-Account Access”
Select “Allows IAM users from a 3rd party AWS account to access this account.”
Enter the following:
Account ID xxx
External ID xxx
Require MFA unchecked
Select “ReadOnlyAccess” from the policy template list and click “Next Step.”
Copy the “Role ARN” value and paste it in the AWS Role ARN field below.
Click “Create Role” in the Amazon IAM console before clicking "Add AWS account" below.
When I click on "Add AWS Account" in stackdriver after creating the role in AWS and pasting in the Role ARN back into stackdriver, I get an error "User is not authorized".
What user is not authorized? Is it that stackdriver can't assume the AWS Role? Is it my Stackdriver account can't add AWS accounts? This is the most useless error message.
I log into my AWS account via AWS account delegation, if that matters. Would this interfere with the stackdriver integration?