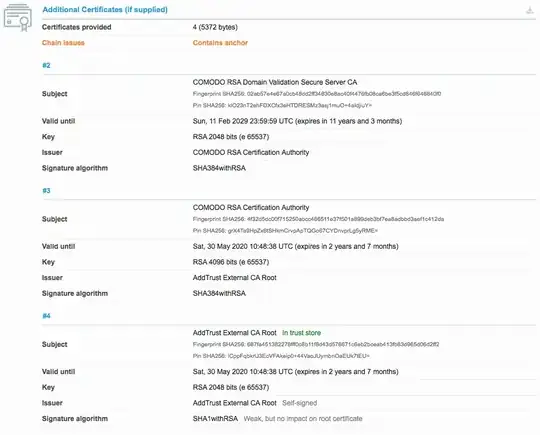
I recently visited the Qualys SSL Server Test to confirm that a Namecheap certificate was installed properly. Everything looked fine except for one chain issue ("Contains anchor"):
It seems that I should be able to resolve this issue by removing the AddTrust External CA Root, which is already present in (most?) trust stores. However, Namecheap's own installation instructions explicitly state that this is one of the three certificates in their CA bundle:
ComodoRSADomainValidationSecureServerCA.crtCOMODORSAAddTrustCA.crtAddTrustExternalCARoot.crt
Is it safe to ignore Namecheap's instructions and remove the AddTrust External CA Root certificate from the chain? If so, why would Namecheap include it in the first place?