There are two issues you could be describing here. The first is someone simply setting up a DNS binding to your IP address. Preventing this in IIS is extremely simple. You simply alter the hostname bindings in IIS such that your content is only served when particular hostnames are requested. There is most likely currently a wildcard binding that you will need to remove as well so that only the bindings you intend can be resolved. (This is also how multiple websites can be hosted on a single IIS web server.)
From IIS connections, you'll be able to right click on a particular site to access the "Edit Bindings..." dialog.
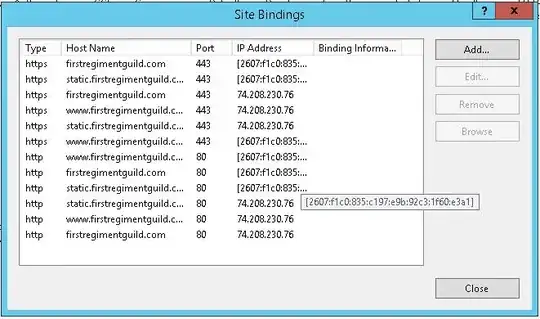
This dialog will show all the bindings setup for what requests this site should respond to. The hostname is the valid hostnames for which the binding should resolve to this site. One site can have many distinct bindings, as seen here.
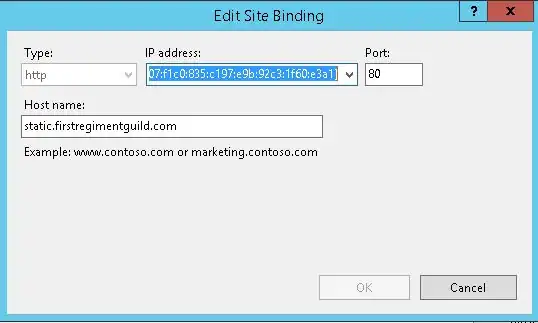
The settings on a particular binding let you set the hostname that should resolve to this site. You can also set things like SSL cert configurations here.
The second possible problem is hot-linking. With hot-linking, it isn't a direct call to your IP address, but rather setting up something on a different domain to reference things on your domain. This can be done through several different means, but most of them require at least some server to be giving instructions prior to accessing your site. Hotlinking is a little bit harder to prevent, but you can set tests about the referrer asking for an asset and only provide the asset if the referrer matches. Since the client browser supplies this information, it will be difficult for a third party to attempt to make the browser provide incorrect information to your server and thus the filtering should be generally effective.


