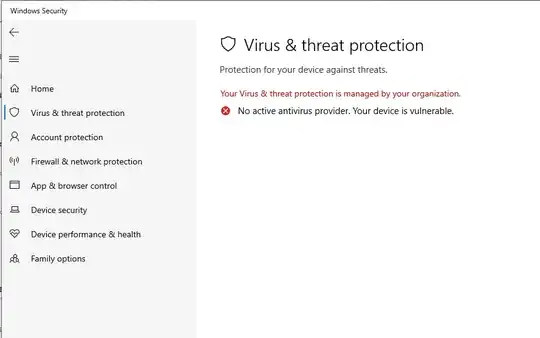
Set-MpPreference -DisableRealtimeMonitoring disables the first one, what are the specific switches to disable the others you see when you open the UI? I have not found a clear example of this in the docs and I don't feel like running EVERY disable switch because MS docs are bad.
-
I had to use "Set-MpPreference -DisableRealtimeMonitoring $true" to disable it on Win10 1809. – KERR Oct 08 '18 at 10:00
7 Answers
After going for hours through the docs: https://docs.microsoft.com/en-us/powershell/module/defender/index?view=win10-ps
Just decided to uninstall it. This works on WS 2016 with PS 5.1.
Remove-WindowsFeature Windows-Defender, Windows-Defender-GUI
The below didn't work for me (from a blog dated 2011-2012), but give it a try before you uninstall:
Get-Service WinDefend | Stop-Service -PassThru | Set-Service -StartupType Disabled
Later edit: Found a way for Windows 10, tested on 20H2 only. Please add a comment if it works for previous builds.
Set-MpPreference -DisableRealtimeMonitoring $true
New-ItemProperty -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender" -Name DisableAntiSpyware -Value 1 -PropertyType DWORD -Force
- 655
- 1
- 11
- 26
from windows server 2016 you could try
uninstall-windowsfeature -name windowsserverantimalware
- 31
- 2
For example you can use something like this - > Run PowerShell console as Administrator - > Paste to console and hit enter
Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend
Full list of options with description available at: https://docs.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=win10-ps
- 31
- 2
I needed to disable Windows defender because I installed a software which I modified with orca (MSI modification), and defender kind of blocked it. Found this "long" solution on this link. I tested it on Windows 10 version 21H2. It gives me then the following answer, which looks good.
Just make a new disableDefender.ps1 file and write the following code inside
if(-Not $($(whoami) -eq "nt authority\system")) {
$IsSystem = $false
# Elevate to admin (needed when called after reboot)
if (-Not ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] 'Administrator')) {
Write-Host " [i] Elevate to Administrator"
$CommandLine = "-ExecutionPolicy Bypass `"" + $MyInvocation.MyCommand.Path + "`" " + $MyInvocation.UnboundArguments
Start-Process -FilePath PowerShell.exe -Verb Runas -ArgumentList $CommandLine
Exit
}
# Elevate to SYSTEM if psexec is available
$psexec_path = $(Get-Command PsExec -ErrorAction 'ignore').Source
if($psexec_path) {
Write-Host " [i] Elevate to SYSTEM"
$CommandLine = " -i -s powershell.exe -ExecutionPolicy Bypass `"" + $MyInvocation.MyCommand.Path + "`" " + $MyInvocation.UnboundArguments
Start-Process -WindowStyle Hidden -FilePath $psexec_path -ArgumentList $CommandLine
exit
} else {
Write-Host " [i] PsExec not found, will continue as Administrator"
}
} else {
$IsSystem = $true
}
67..90|foreach-object{
$drive = [char]$_
Add-MpPreference -ExclusionPath "$($drive):\" -ErrorAction SilentlyContinue
Add-MpPreference -ExclusionProcess "$($drive):\*" -ErrorAction SilentlyContinue
}
Write-Host " [+] Disable scanning engines (Set-MpPreference)"
Set-MpPreference -DisableArchiveScanning 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableBehaviorMonitoring 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableIntrusionPreventionSystem 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableIOAVProtection 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableRemovableDriveScanning 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableBlockAtFirstSeen 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableScanningMappedNetworkDrivesForFullScan 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableScanningNetworkFiles 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableScriptScanning 1 -ErrorAction SilentlyContinue
Set-MpPreference -DisableRealtimeMonitoring 1 -ErrorAction SilentlyContinue
Write-Host " [+] Set default actions to Allow (Set-MpPreference)"
Set-MpPreference -LowThreatDefaultAction Allow -ErrorAction SilentlyContinue
Set-MpPreference -ModerateThreatDefaultAction Allow -ErrorAction SilentlyContinue
Set-MpPreference -HighThreatDefaultAction Allow -ErrorAction SilentlyContinue
$need_reboot = $false
# WdNisSvc Network Inspection Service
# WinDefend Antivirus Service
# Sense : Advanced Protection Service
$svc_list = @("WdNisSvc", "WinDefend", "Sense")
foreach($svc in $svc_list) {
if($(Test-Path "HKLM:\SYSTEM\CurrentControlSet\Services\$svc")) {
if( $(Get-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$svc").Start -eq 4) {
Write-Host " [i] Service $svc already disabled"
} else {
Write-Host " [i] Disable service $svc (next reboot)"
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$svc" -Name Start -Value 4
$need_reboot = $true
}
} else {
Write-Host " [i] Service $svc already deleted"
}
}
Write-Host " [+] Disable drivers"
# WdnisDrv : Network Inspection System Driver
# wdfilter : Mini-Filter Driver
# wdboot : Boot Driver
$drv_list = @("WdnisDrv", "wdfilter", "wdboot")
foreach($drv in $drv_list) {
if($(Test-Path "HKLM:\SYSTEM\CurrentControlSet\Services\$drv")) {
if( $(Get-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$drv").Start -eq 4) {
Write-Host " [i] Driver $drv already disabled"
} else {
Write-Host " [i] Disable driver $drv (next reboot)"
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$drv" -Name Start -Value 4
$need_reboot = $true
}
} else {
Write-Host " [i] Driver $drv already deleted"
}
}
# Check if service running or not
if($(GET-Service -Name WinDefend).Status -eq "Running") {
Write-Host " [+] WinDefend Service still running (reboot required)"
$need_reboot = $true
} else {
Write-Host " [+] WinDefend Service not running"
}
$link_reboot = "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\disable-defender.lnk"
Remove-Item -Force "$link_reboot" -ErrorAction 'ignore' # Remove the link (only execute once after reboot)
if($need_reboot) {
Write-Host " [+] This script will be started again after reboot." -BackgroundColor DarkRed -ForegroundColor White
$powershell_path = '"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"'
$cmdargs = "-ExecutionPolicy Bypass `"" + $MyInvocation.MyCommand.Path + "`" " + $MyInvocation.UnboundArguments
$res = New-Item $(Split-Path -Path $link_reboot -Parent) -ItemType Directory -Force
$WshShell = New-Object -comObject WScript.Shell
$shortcut = $WshShell.CreateShortcut($link_reboot)
$shortcut.TargetPath = $powershell_path
$shortcut.Arguments = $cmdargs
$shortcut.WorkingDirectory = "$(Split-Path -Path $PSScriptRoot -Parent)"
$shortcut.Save()
} else {
if($IsSystem) {
# Configure the Defender registry to disable it (and the TamperProtection)
# editing HKLM:\SOFTWARE\Microsoft\Windows Defender\ requires to be SYSTEM
Write-Host " [+] Disable all functionnalities with registry keys (SYSTEM privilege)"
# Cloud-delivered protection:
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" -Name SpyNetReporting -Value 0
# Automatic Sample submission
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection" -Name SubmitSamplesConsent -Value 0
# Tamper protection
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows Defender\Features" -Name TamperProtection -Value 4
# Disable in registry
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows Defender" -Name DisableAntiSpyware -Value 1
Set-ItemProperty -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender" -Name DisableAntiSpyware -Value 1
} else {
Write-Host " [W] (Optional) Cannot configure registry (not SYSTEM)"
}
if($MyInvocation.UnboundArguments -And $($MyInvocation.UnboundArguments.tolower().Contains("-delete"))) {
# Delete Defender files
function Delete-Show-Error {
$path_exists = Test-Path $args[0]
if($path_exists) {
Remove-Item -Recurse -Force -Path $args[0]
} else {
Write-Host " [i] $($args[0]) already deleted"
}
}
Write-Host ""
Write-Host "[+] Delete Windows Defender (files, services, drivers)"
# Delete files
Delete-Show-Error "C:\ProgramData\Windows\Windows Defender\"
Delete-Show-Error "C:\ProgramData\Windows\Windows Defender Advanced Threat Protection\"
# Delete drivers
Delete-Show-Error "C:\Windows\System32\drivers\wd\"
# Delete service registry entries
foreach($svc in $svc_list) {
Delete-Show-Error "HKLM:\SYSTEM\CurrentControlSet\Services\$svc"
}
# Delete drivers registry entries
foreach($drv in $drv_list) {
Delete-Show-Error "HKLM:\SYSTEM\CurrentControlSet\Services\$drv"
}
}
}
Write-Host "Script Finished" -foregroundcolor Yellow
- 125
- 1
- 8
-
I can't downvote, but here's my warning: This script breaks the service completely for me. I'm unable to turn it back on after running the script even after a reboot. – Alan Jun 11 '22 at 13:25
-
1Actually there is an update to my post. I did not mention that Windows made it on purpose impossible to turn completely off Windows defender's real time protection, you can only turn off some features like cloud based protection, but it will always remain active somehow, even with this script. to be able to turn it off completely you must manually turn off "Tampler protection", because this is what windows wants to avoid, to be able to turn off Defender protection by script. Now I am not saying that its not possible with any kind of malware, kali linux attack or something like that. – Andy McRae Jun 13 '22 at 13:13
-
To answer your question, you should be able to turn it on again manually but the script makes some reboot tasks. To avoid it get to this path "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp" and delete \disable-defender.lnk script because this causes the defender of windows to turn off completely – Andy McRae Jun 13 '22 at 13:18
-
This script worked well for me, but you need to run it in Windows Safe mode. – George Y. Sep 15 '22 at 02:54
To disable Real-time Protection
Set-MpPreference -DisableRealtimeMonitoring $true
Disable Automatic Sample Submission
Set-MpPreference -SubmitSamplesConsent NeverSend
Disable Cloud-Based Protection
Set-MpPreference -MAPSReporting Disable
Verified on Win11 Enterprise 22H2 default install:
Since WinDefend is a special protected app, the supported ways to disable are via SCCM/Intune/etc, or when different AV used instead.
So only possible complete solution requires: sc.exe, & another app with TI rights, so we can modify relevant services: Nirsoft - AdvancedRun
We need to make 2 files:
%windir%\script-ps with contents:
Set-MpPreference -DisableRealtimeMonitoring $true
Get-Service WinDefend | Set-Service -StartupType Disabled
Get-Service Sense | Set-Service -StartupType Disabled
Get-Service mpssvc | Set-Service -StartupType Disabled
Get-Service WdNisSvc | Set-Service -StartupType Disabled
sc.exe config WinDefend binPath=%windir%\bfsvc.exe
NoDefend.cfg with contents:
[General]
EXEFilename=
CommandLine=(gc script-ps) | iex
StartDirectory=%windir%
WaitProcess=0
PriorityClass=32
WindowState=0
UseWindowPosition=0
WindowPosition=20,20
UseWindowSize=0
WindowSize=640,400
RunAs=8
RunAsProcessName=
EnvironmentVariablesMode=1
OSCompatMode=0
UseSearchPath=0
ParseVarCommandLine=1
UseAffinityMask=0
AffinityMask=0 1
Compat640480=0
CompatDisableVisualThemes=0
CompatDisableDesktopComp=0
CompatDisableFullScreenOpt=0
CompatHighDPI=0
CompatColors=0
RunAsUserName=
RunAsDomain=
RunFromService=0
ComputerName=
RunMode=4
ShellExecuteAction=
CommandWindowMode=2
[EnvironmentVariables]
Lines=0
WinPos=2C 00 00 00 00 00 00 00 01 00 00 00 FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF 65 00 00 00 18 00 00 00 9A 03 00 00 A0 02 00 00
Now run this in CMD - Admin:
AdvancedRun.exe /Run NoDefend.cfg
Hidden PS window runs & execs cmds (not script so no need to bypass PS restrictions) in %windir%\script-ps
Wait a second for it all to run, then reboot, & then all except WinDefend will be disabled. Somehow WinDefend will be set to Manual, & so it tries starting, but fails since we changed its exe to different lolbin that does nothing with 0 args. Ignore that service: We have great success of "completely turned off Windows Defender"
While this works for now, it might not in future if M$ patches this "Answer".
If you want to re-enable again, change the cmds to Enable & change binPath to its current location, like:
"C:\ProgramData\Microsoft\Windows Defender\Platform\<version>\MsMpEng.exe"
- 41
- 8
It's not recommended to turn off Windows Defender completely as it provides essential security features to your Windows operating system. However, if you need to disable it temporarily for troubleshooting or other reasons, you can do so using PowerShell with administrator privileges.
Here's how you can disable Windows Defender using PowerShell:
Open PowerShell as an administrator. You can do this by right-clicking on the PowerShell icon and selecting "Run as Administrator".
Use the following command to disable real-time protection for Windows Defender:
sql Copy code Set-MpPreference -DisableRealtimeMonitoring $true This will turn off real-time protection for Windows Defender.
Use the following command to disable the cloud-based protection feature for Windows Defender:
sql Copy code Set-MpPreference -DisableIntrusionPreventionSystem $true This will disable the cloud-based protection feature for Windows Defender.
Finally, use the following command to disable Windows Defender completely:
sql Copy code Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true This will disable both real-time protection and cloud-based protection features for Windows Defender.