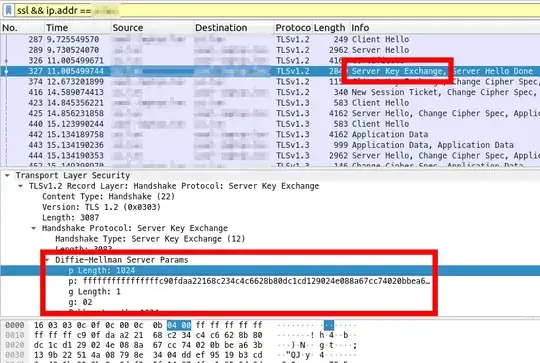
How can I validate that I've properly setup my Apache 2.4.6 server with a custom 2048-bit (or 4096-bit) dhparams config?
Following the weakdh.org sysadmin guide, I created my own dhparams.pem file with openssl dhparam -out dhparams.pem 2048. The guide says to add this to the apache mod_ssl config with SSLOpenSSLConfCmd DHParameters "{path to dhparams.pem}", but this is only valid for Apache >= v2.4.7. I'm using CentOS 7, which uses Apache v2.4.6.
According to this server fault question, the solution in Apache v2.4.6 is to append it to the certificate file. So I did a cat /etc/pki/dhparam/dhparam.pem >> /etc/letsencrypt/live/openbuildinginstitute.org/cert.pem (and also cat /etc/pki/dhparam/dhparam.pem >> /etc/letsencrypt/live/openbuildinginstitute.org/fullchain.pem` && restarted apache.
But how do I verify from the client-side (my browser) that this config is in effect?
This is especially an issue as we use Let's Encrypt, so we want to make sure our 90-day cert renewals include this step, and I want to be able to verify it from the browser.
I already tried downloading the certificate with firefox's "View Certificate" -> "Details" -> "Export...", and I confirmed that the "-----BEGIN DH PARAMETERS-----" was absent from the resulting file.