BACKGROUND
I have a website which is up and running and has a SSL certificate that I bought, I didn't know about Let's Encrypt at the time.
I am planning a re-write of the application. I'm moving it to ReactJS, so I am building a .Net Core API to drive that.
ISSUE
I wish the api to sit at https://api.bejebeje.com, so I went ahead and using Certify SSL Manager got myself an SSL certificate.
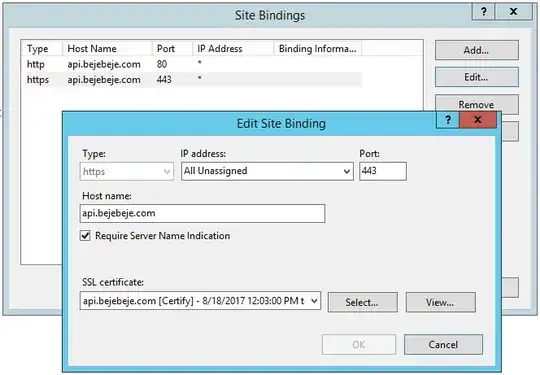
My bindings look like this:
I can access my site via https://api.bejebeje.com/api/artists/ but the SSL isn't green in Chrome or Firefox, it says I have a name mismatch.
Why is this happening and how do I fix it?
Any help would be greatly appreciated.