I've received email from aws which says my aws s3 buckets are configured to allow read access to anyone on internet and have asked me to review the ACL and secure it. Basically my s3 buckets are being used as backend for cloudfront distribution. Below are my s3 buckets which are having the same ACL applied on them with same policy.
media-example-com
font-example-com
blog-example-com
app-assets-example-com
Common policy is as below applied on all the buckets.
{
"Version": "2008-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::<bucket-name>-example-com/*"
}
]
}
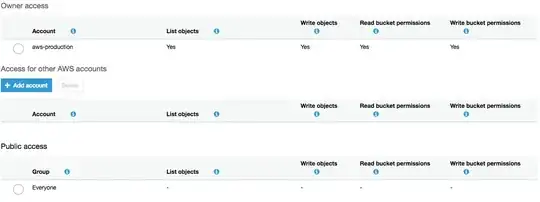
And below is ACL screenshot which is common to all those buckets.
I don't understand what exactly aws support means when it says those buckets are configured to allow read access from internet. When in screenshot its clear that read access is not allowed.