I am creating a site with my own CA and signing client certs with it. The clients will need to add my CA as a trusted source, but for security reasons I don't want them to blindly trust everything that could be signed with the CA key, so I want to impose limitations to build clients' trust. So I want to limit the CA abilities to just signing client certs and enabling https access. I am not sure all restrictions I should impose in the cert creation.
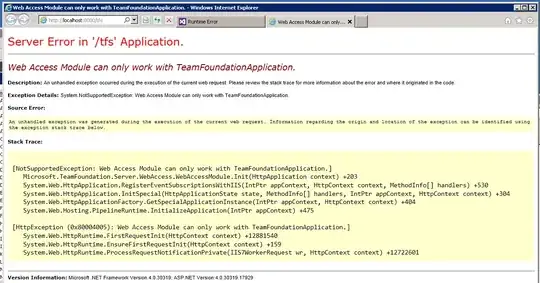
The best way to do it seems to be Name constraints, and use a white list to limit the usage, which is apparently respected nowadays. So I though I have to use a dns (let's say xyz.com), so the CA signature would not be accepted for google.com f.ex, and put that also in each SAN of the client certificates, so the client certs are considered valid and not rejected. Apparently that's not how it works. I have tried this but I have not been able to make it work correctly. Also, I am getting a warning from Windows... Maybe it is because all possible name constraint types must be present?
So my questions are:
- How should I configure the CA cert? What restrictions should I apply in the CA cert to limit its ability to be misused? If it involves name constraints, why is my example in the image not working?
- Is there anything extra that should be done/considered in the client certs, like adding an extra SAN?
EDIT
Ideally, there should be something in my CA certificate that forces it to only sign client certificates and do the https server authentication. I don't see how to make this limitation, I think it is not possible.
For the use of Name constraints, I have use xyz.com as permitted, and I thought that only certs signed by my CA with SAN xyz.com and actually used by using that name will be accepted (otherwise I could create a certificate with SAN xyz.com and google.com and might work when accessing google.com). So I have used a client certificate signed by my CA with no SAN xyz.com and I was accepted. Not sure if the name constraints apply in this case too.