I am having a very hard time getting clear about receive connectors in Exchange 2010, which I have unhappily inherited.
I have read a lot of articles and books, but nothing presents the information I need in a clear way, and some of the articles are conflicting, which is expected but doesn't make this any easier.
The reason for asking these questions together is that some of them impact others, and if asked separately they would probably not make clear what I need to accomplish.
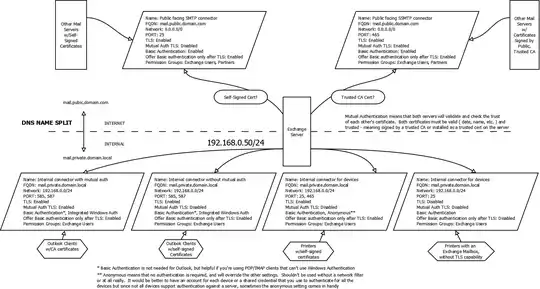
My Exchange server is Hub role internet-facing. There is no edge or filter between it and the outside.
I recently implemented split DNS, and I want to know if the "Server" and "Fqdn" attributes should be changed to the public DNS name for my mail server, as in "mail.domain.com".
The "Name" attribute is only a label for the connector which shows in the Exchange Management Console.
The "Identity" attribute is related to the GUID. Again, it currently shows as \<"Name" attribute>. The question is whether I can change that to the public DNS name for my mail server, "mail.domain.com".
I need to know if the DistinguishedName attribute can or should also be changed.
Some of my existing connectors have a value for the "DistinguishedName" attribute which reads "CN=,CN=SMTP Receive Connectors,CN=Protocols,CN=,CN=Servers,CN=Exchange Administrative Group,(...),CN=Administrative Groups,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=,DC=". I know that at one point a migration was done from Exchange 2003, and that it was not cleaned up, so to speak. I need to know if I can simply remove connectors with that value, or whether they need to be replaced with other ones.
The "Default" connector, as I understand it, receives email from the internet on port 25 from any IP (0.0.0.0-255.255.255.255).
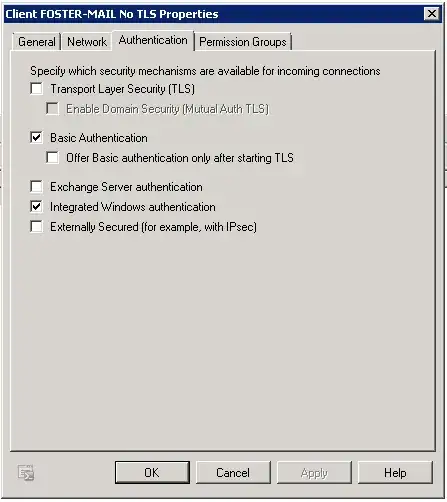
I need to understand how AuthMechanism, RequireTLS and PermissionGroups relate to each other, and where RequireTLS is appropriate, as in I don't want to lose email by forcing TLS.
I want to configure TLS. I need to understand where "opportunistic" vs "mutual" applies, as in do I use it for both internet and internal, or only internet.
I want to understand which values should be set for the "AuthMechanism" attribute, and why, given that I want to configure TLS.
I have internal applications which I think need separate connectors, from what I have read. I need to know if that is true, and how to configure that.
I have multifunction printers which send scans via email, which I think also need separate connectors, and I need to know how to configure that.
I have a third party who needs to send email using my DNS name and IP, which I think is called "relay". I need to know if that is correct, and how to configure it.
Links to articles which don't present specific instructions on how to accomplish what I listed above are not helpful.
Explanations of how these connectors are used for my specific needs are very helpful, and I appreciate the help.