Every time I setup a new Linux host (CentOS, lately), expecially when such an host will have some roles within our small datacenter (around 100 hosts), I take care to:
- install the ntp package;
- add, on top of the server list, a new server instance pointing:
- to our more-or-less official Italian ntp server (
time.ien.it), if the system has outbound ntp access; - to an "internal-host", who acts like a sort of official ntp "internal" server, if the system is not Internet-connected.
- to our more-or-less official Italian ntp server (
- enabling the ntp service, so to properly deals with reboots
So, as for systems with Internet access, the server-list configured in the ntp.conf is the following:
server time.ien.it iburst
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
While investigating completely different issues, I discovered that above configuration generate traffic to remote hosts I'm totally unaware of.
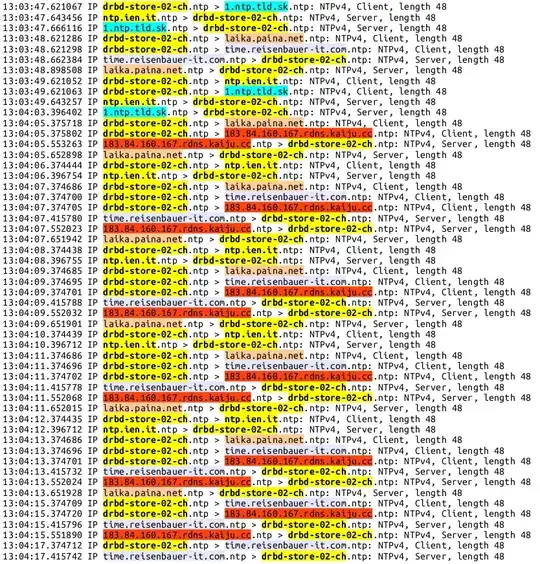
Here is a snippet of a tcpdump capture, taken on the outbound interface of our drbd-store-02-ch host:
where you can see:
- traffic from/to hosts I'm correctly expecting (the "yellow" one);
- traffic from/to hosts that looks unrelated to CentOS and/or ntp.org domain. Specifically:
1.ntp.tld.sklaika.paina.nettime.reisenbauer-it.com183.84.160.167.rdns.kaiju.cc
During investigation, it cames out that there where also other hosts, not included in the list above. I even found hosts whose reverse hostname clearly pointed to some big ISPs, referring to VPSs and stuff like that.
So my questions are:
- Should I remove the default server-list and rely only to my "trusted"
time.ien.itexternal ntp-server host? - if not, how can I be sure that those remote hosts are effectively "safe" and properly protected/managed... so to not put at risk my ntp-service-requests?
P.S.: as a side note, I'm absolutely aware about the DNS resolution process and so the problem is not "why" I'm contacting those servers. The problem is: "is it safe?"