Here's the setup -- 3 servers on Microsoft Azure:
- Domain Controller (Server 2016)
- ADFS (using gMSA account) (Server 2016, latest ADFS)
- ADFS Proxy (Server 2016, latest ADFS Proxy)
I'm able to connect the ADFS proxy no problem to the ADFS server, however, I have an intermittent error (seems to fail every other sync request) between the ADFS Proxy and the ADFS server.
Every few minutes as the ADFS Proxy works to sync it's proxy config data, I get two entries in Applications & Services Logs -- AD FS --> Admin
The failure to sync event:
The federation server proxy configuration could not be updated with the latest configuration on the federation service.
Additional Data
Error:
Retrieval of proxy configuration data from the Federation Server using trust certificate with thumbprint '8D4D65367FC31B61230951832C81E2B0891E3B9F' failed with status code 'InternalServerError'.
The successful sync event:
The federation server proxy successfully retrieved and updated its configuration from the Federation Service 'adfs.testdomain.com'.
I've ran the PowerShell script from this troubleshooting guide and no errors have been detected. None of the other issues mentioned there are applicable either. https://blogs.technet.microsoft.com/applicationproxyblog/2014/05/28/understanding-and-fixing-proxy-trust-ctl-issues-with-ad-fs-2012-r2-and-web-application-proxy/
I've initialized and checked device registration as well and that seems to be functional on the ADFS server.
Here's what I can and can't do:
- On ADFS server, I can load and login to the Web SSO page.
- On ADFS Proxy, I cannot login to the Web SSO page(https://adfs.testdomain/adfs/ls/idpinitiatedsignon.htm)
- From roaming PC's, I cannot connect to the ADFS Proxy's Web SSO page, but I can resolve the DNS no problem. Chrome/etc. show a "the page took too long to respond" error.
- From roaming PC's, I cannot join them to the domain via the ADFS Proxy.
Any ideas? Thank you!
Additional Details
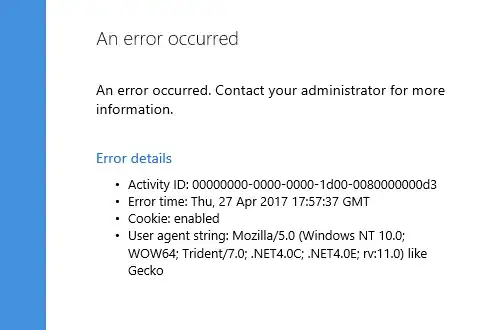
I've reinstalled everything. On the ADFS server I get this error when navigating to the SSO login page:
Also getting this error message from the ADFS server:
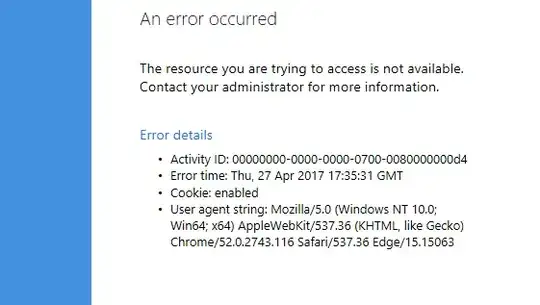
From client PC's trying to load the SSO page I get this error when navigating to the SSO login page:
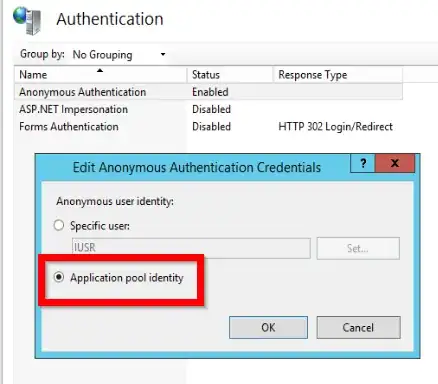
Edit: Here's another update with more info (ADFS properties). Still having issues with proxy trust (same success/failure events as above) and still unable to join devices to the domain (likely related).