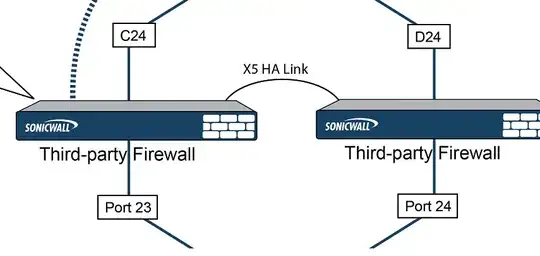
Following the comment, there is a better preview of what you need.
You miss one detail, does you have bought the Active/Active for the HA ?
- With it you need two interface mapped to make the HA. One for FailOver, and the second will allow Active/Active mode, that the running state will be know by each firewall, so it's a hot move without interruption for any internet transaction. Without that licence and configuration the router work in Active / Passive mode and the state is lost if the active's switch. It's not really important if your user do simple youtube.com streaming or such, but for ssl transaction, or like RDP session the user will see an interuption and will be maybe asked to re-login
For the VLAN you route by your two interface you need that :
- Make a portshield group for those two ports on each unit.
- Make each VLAN know by the interface for the route back.
[Modem Cable 1] --- [Switch VLAN Internet 1]
[Modem Cable 2] --- [Switch VLAN Internet 2]
[NSA 1 5600 WAN 1] --- [Switch VLAN Internet 1]
[NSA 1 5600 WAN 2] --- [Switch VLAN Internet 2]
[NSA 1 5600 LAN 1] (portshield - bridging)
--- [Switch 1 Trunk (LAN VLAN)] (spanning-tree active) >
[NSA 1 5600 LAN 2] (portshield - bridging) --- [Switch 2 Trunk (LAN VLAN)] (spanning-tree active)
[NSA 2 5600 WAN 1] --- [Switch VLAN Internet 1]
[NSA 2 5600 WAN 2] --- [Switch VLAN Internet 2]
[NSA 2 5600 LAN 1] (portshield - bridging)
--- [Switch 1 Trunk (LAN VLAN)] (spanning-tree active)
[NSA 2 5600 LAN 2] (portshield - bridging)
--- [Switch 2 Trunk (LAN VLAN)] (spanning-tree active)
[NSA 1 xX] --- [NSA 2 xX] One link for basic HA/FailOver. (xX is the interface
you choose to be used for HA) (For basic HA (Active/Passive))
[NSA 1 xX] --- [NSA 2 xX] A second HA uplink if you can do
Active/Active (xX is the interface you choose to be used for HA)
And dont forget to stack your NSA 5600 with the HA mode.
A bit like shown in that picture