I just created a simple postgres database.
It gave me a link that I could use to connect to it, so I tried connecting using pgadmin but it gives a timed out error.
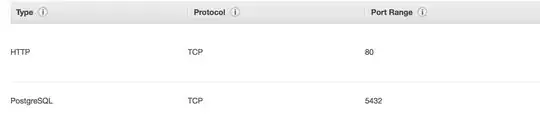
So, I read the documentation again and I've made sure that my VPC security group is correct. It has an inbound rule - postgres port 5432 on a security group sg-something-something.
However, that still wasn't working. Now, I've added one more inbound rule postgres port 5432 on myIP and that lets me log into the database.
Is this really the right approach?