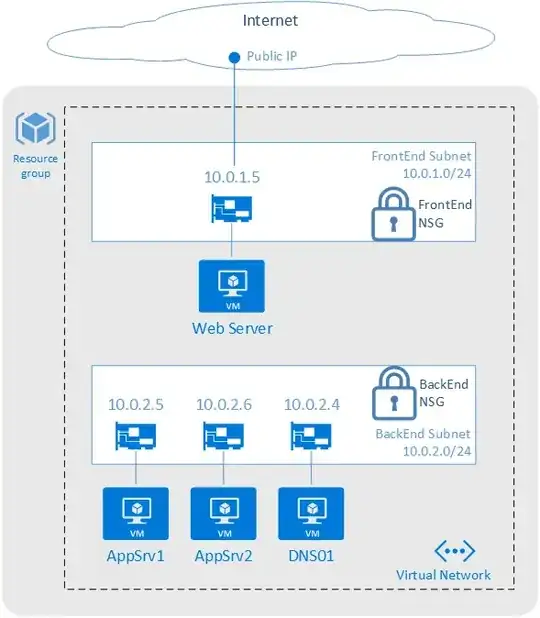
I'm building a network of VM's in Azure, 1 group of VM's for the webtier and 1 group of VM's for the data/sql-tier. I will create a jumpbox VM that enables access for devops purposes via VPN.
Now I read that I should have minimal software and connection-options to my actual VM, as it should run via the jumpbox to minimize the attack surface of my VM's and to have a central access point.
Now I want to do 2 things:
Connect via Remote Desktop to all my VM's, I figured I can simple create a VPN RDP connection to my jumpbox, and when logged into my jumpbox, simply open another RDP window to my other VM's using the internal v-network IP.
Access my (loadbalanced w/ availability set) MSSQL 2016 instance directly via SQL Server Management Studio or an application using a connection string. The MSSQL instance lives on my sql-tier VM, not on my jumpbox, can I somehow forward SQL traffic from my jumpbox to my sql-tier VM? I would guess that accessing the sql-tier VM directly goes against the whole idea of having a jumpbox.
Notes: - running MS SQL Server 2016 on Windows Server 2016