Problem
I need to access multiple different VPN networks simultaneously, mainly for HTTP and sometimes SSH. Further, I am not allowed to use openvpn on my workstation (no legal restriction, rather an infrastructure issue). Port forwardings are fine.
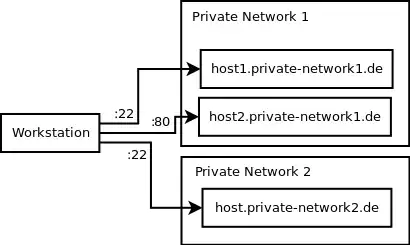
The following diagram is an attempt to picture the involved parties. My workstation wants to access host1.private-network1.de and host2.private-network1.de which are not visible to the internet. The institution requires me to enter their VPN for accessing this machine. The same applies for the third host in the second private network. I need to access the machine on port 22 but this is only possible inside the VPN.
My Intended Solution
(Other solutions are also perfectly fine)
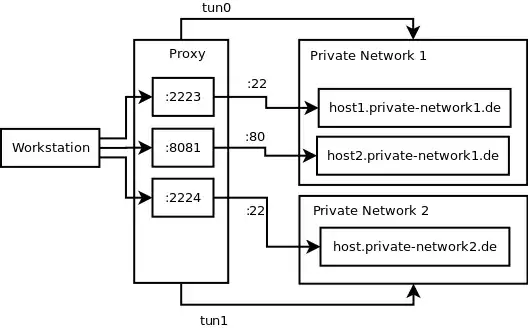
I plan on using a proxy server under my control (e.g. a RPI) to connect to the different networks via openvpn. In place, the proxy server allows for port forwardings using SSH. On my workstation I could now setup port forwardings like:
The question is how to configure multiple OpenVPN networks in Linux, such that I can use simple port forwardings (as shown in the picture) to access different hosts in different private networks. The VPNs should only be used for this port forwardings. The remaining traffic on the proxy host (like updates) should not be routed via any of these VPN connections. It is even desirable that all the remaining traffic could still be routed via a third VPN, but this may be another question.
OT: Happy Christmas :)