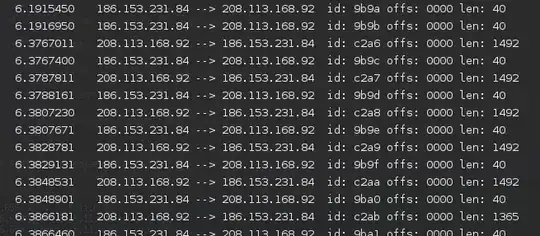
I was playing around with dpkt in Python, trying to decode PPPoE - and the program was working just fine, till I noticed that the Offset in the encapsulation IP packets was always 0, even with clearly fragmented packets.
As can be seen, the server is sending 1492-byte packets (because of the PPPoE encapsulation, I suppose), and a last packet of 1365. But offset is always 0 - shouldn't it be increasing?
Of course I suspected my program, but I checked the same transfer with Wireshark and got the same result.
Am I interpreting this the wrong way?