Can someone spot a mistake in the Powershell command trying to extract pwdLastSet from Active Directory for some users?
For some accounts it works:
PS C:\> get-aduser -filter "name -like 'Admin*'" -Properties pwdLastSet | Select -first 1 name,pwdLastSet | format-list
name : Administrator
pwdLastSet : 131254235816382539
For some it doesn't:
PS C:\> get-aduser -filter "name -like 'G*Ol*'" -Properties pwdLastSet | Select -first 1 name,pwdLastSet | format-list
name : Grzegorz Olędzki
pwdLastSet :
What needs to be noted, that the property seems to be set when retrieved from GUI:
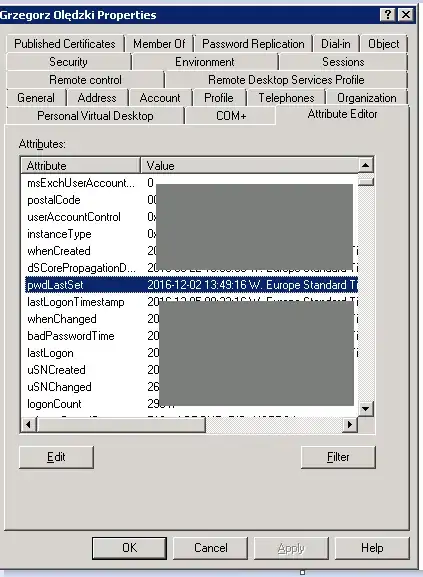
The problem consistently affects multiple accounts, so I suspect there's something I simply don't understand.