I have an Amazon Web Services S3 bucket I want to use with the android data syncing app 'FolderSync'.
Towards that I want to set limited perms on the bucket for a new user.
Within the AWS management console I can create the user but the only S3 related permissions I can find to assign to that user are :
- AmazonS3FullAccess ("Provides full access to all buckets via the AWS Management Console.")
- AmazonS3ReadOnlyAccess ("Provides read only access to all buckets via the AWS Management Console.")
Neither of which sound like what I want (I don't want access via the console for this user and I don't want it for 'all buckets').
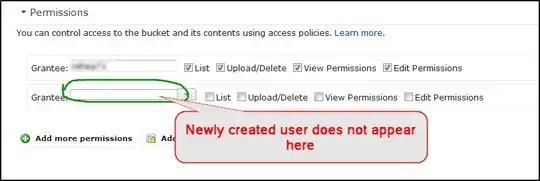
If I don't set any permissions for this user I get a warning message but otherwise I am able to complete the user creation however when I then go to the buckets to assign rights to that user the new user doesn't appear in the dropdown list (as shown below).
There must be a way to do this - can anybody help ?