Application Server role has been deprecated in Windows Server 2012 R2 as you already noted, though there is no indication as to where role features are moved or how they are named now. Documentation just says: "The Application Server role is deprecated and will eventually no longer be available as an installable server role. Instead, install individual features and roles separately."
Though by looking at Server 2012 R2 installation I was able to find all the features you mentioned anyway, but it seems it is in Server 2016 where we see "no longer be available as an installable server role" part really implemented - so there out of all role features/components mentioned by you I was only able to find that AS-WAS-Support from 2012 R2 renamed to WAS in Server 2016 this one is exactly what you need, i.e. Windows Process Activation and it includes exactly the same sub components in Server 2016. Screenshot of Get-WindowsFeature output:
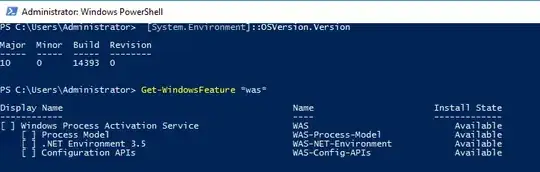
If you execute Dism /online /Get-Features you also should be able to see WAS* features somewhere in between other IIS* features:
I think some functionality could have been merged into other features but maybe not. If you have software product requiring this role likely it does not have support for recently RTMed Server 2016 - you may work with vendor to get statement on supportability, if you have access to MSFT support just request them for information about where are all the features mentioned by you in Server 2016 and whether they all were they all removed or what.
Based on how it is worded in documentation mentioned above it is quite valid to ask MSFT to update their documentation to explain exactly where all the sub-components in Server 2016 as it does not seem to be the case that we can "install individual features and roles separately".
Additional section of MSFT documentation "Features Removed or Deprecated in Windows Server 2016" does not add any clarifications on Application Server role, referring back to the list of what has been deprecated in 2012 R2 & 2012.

